KMIP integration is an Enterprise-only feature. Please reach out to
sales@infisical.com if you have any questions.
How KMIP Works with Infisical
At a high level, the KMIP integration follows this architecture: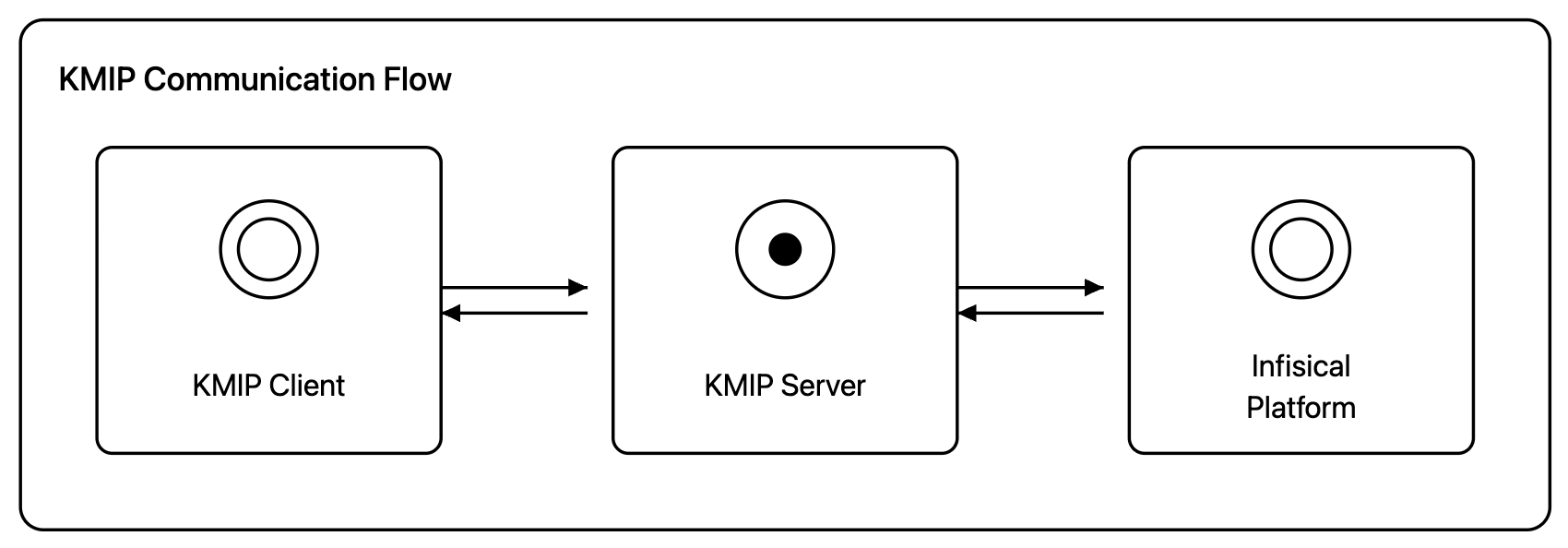 At a high level, the KMIP integration works as follows:
At a high level, the KMIP integration works as follows:
- KMIP clients (your applications or tools) communicate with the KMIP server
- The KMIP server acts as a proxy and forwards requests to Infisical KMS
- The KMIP server authenticates to Infisical using a machine identity
infisical kmip start command) and serves as an intermediary between your KMIP clients and Infisical’s key management system.
Supported Operations
The Infisical KMIP server supports the following operations for symmetric keys:- Create - Generate symmetric keys
- Register - Register externally created keys
- Locate - Find keys using attributes
- Get - Retrieve keys securely
- Activate - Enable keys for usage
- Revoke - Revoke existing keys
- Destroy - Permanently remove keys
- Get Attributes - Retrieve metadata associated with keys
- Query - Query server capabilities and supported operations
Compatibility
Infisical KMIP supports KMIP versions 1.0 to 1.4, ensuring compatibility with a wide range of clients and security tools.Network Requirements
Ensure the following network connectivity is in place:- KMIP Client → KMIP Server: KMIP clients must be able to reach the KMIP server on port 5696 (or your configured port). Ensure firewalls allow this traffic and DNS resolution works if using hostnames.
- KMIP Server → Infisical Platform: The KMIP server needs outbound HTTP access to Infisical. For self-hosted instances, ensure connectivity to your custom domain.
Configure and Deploy the KMIP Server
Follow these steps in order to set up KMIP integration with Infisical:Enable KMIP at the Organization Level
First, you need to enable KMIP for your entire Infisical organization and set up its PKI infrastructure.Navigate to Organization Settings > KMIP and click Setup KMIP.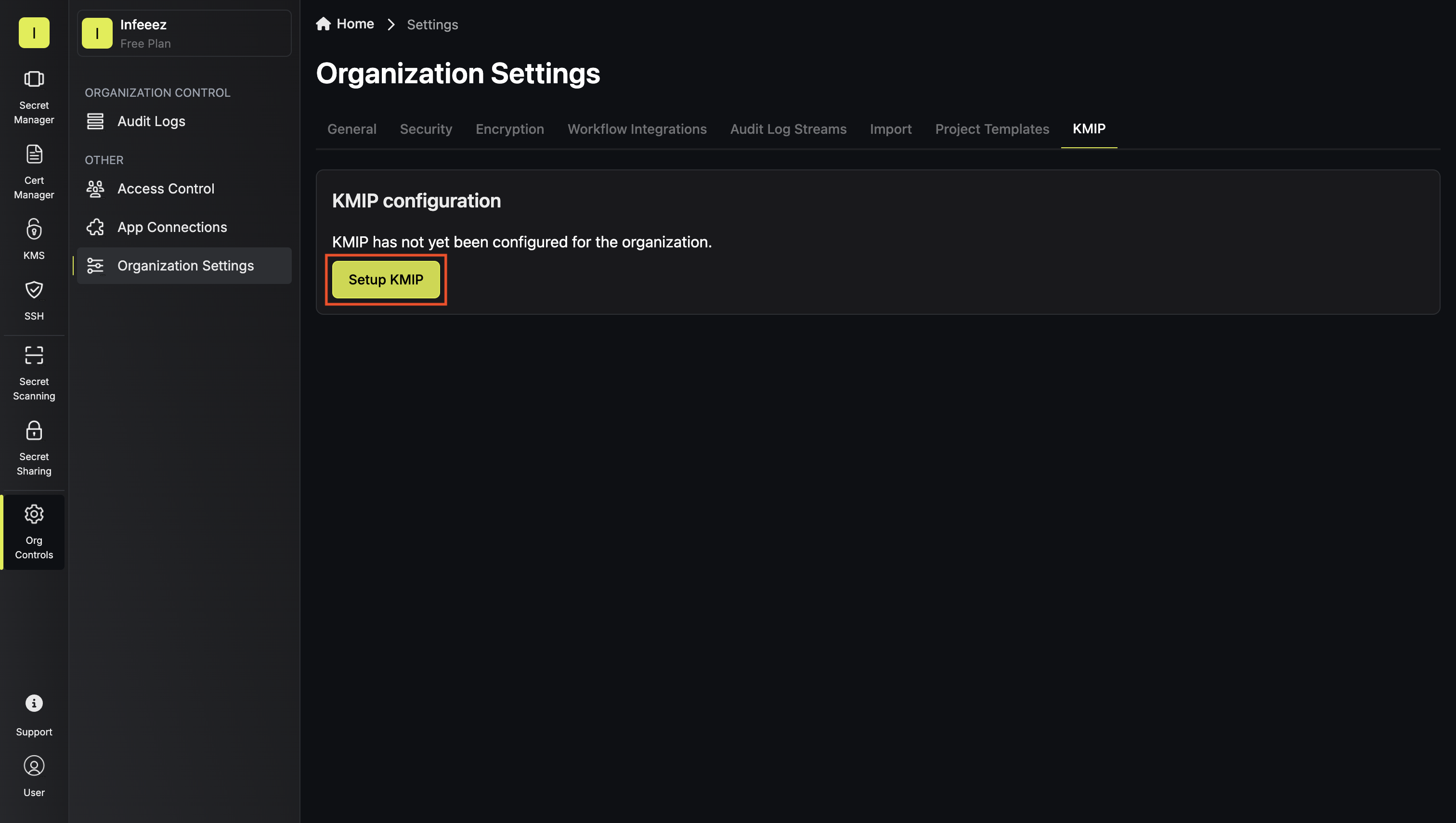 In the modal, select the desired key algorithm to use for the KMIP PKI of your organization, then click Continue.
In the modal, select the desired key algorithm to use for the KMIP PKI of your organization, then click Continue.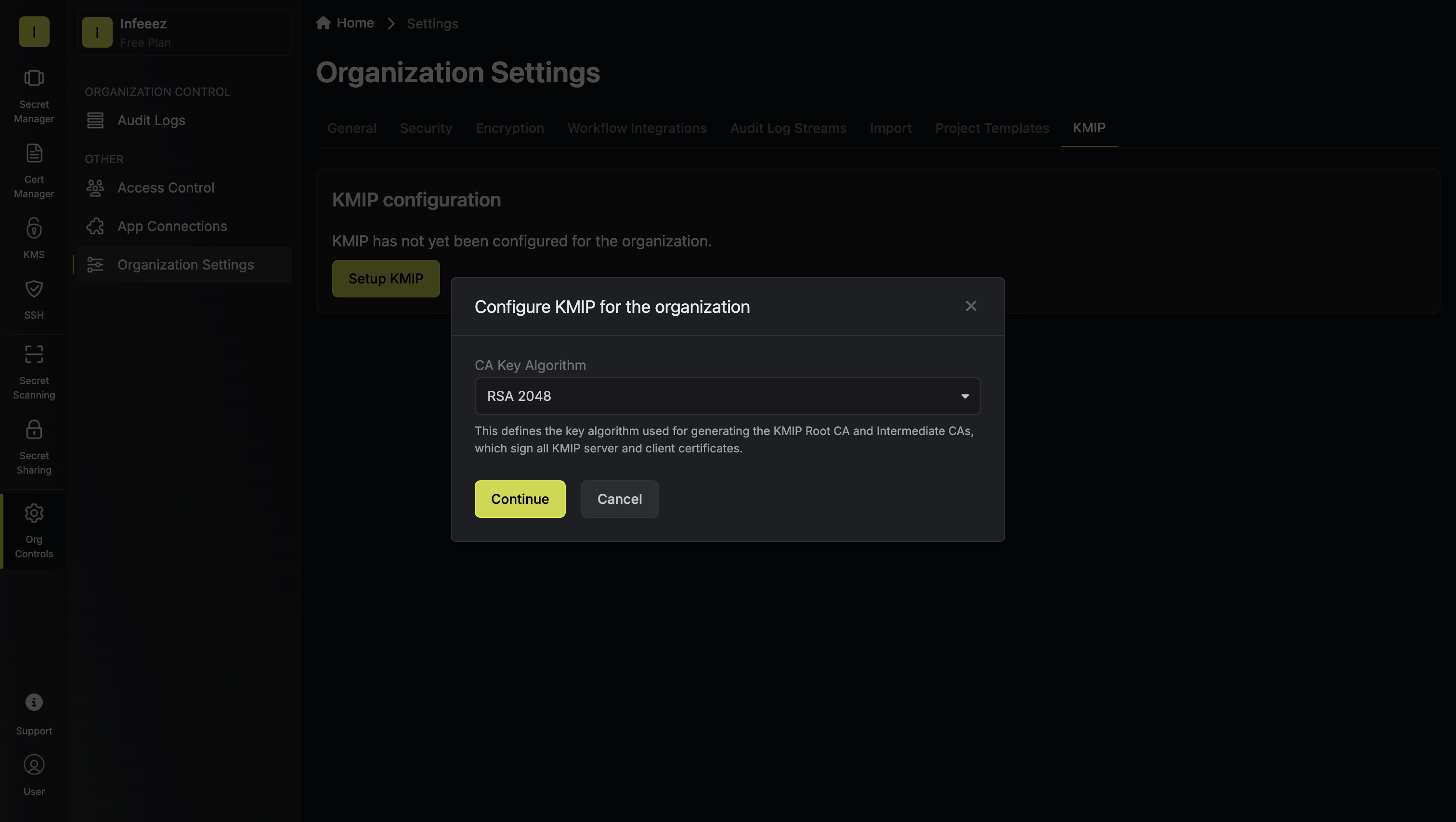 This generates the KMIP PKI for your organization, creating the cryptographic foundation that will be used for secure KMIP communications.
This generates the KMIP PKI for your organization, creating the cryptographic foundation that will be used for secure KMIP communications.
 In the modal, select the desired key algorithm to use for the KMIP PKI of your organization, then click Continue.
In the modal, select the desired key algorithm to use for the KMIP PKI of your organization, then click Continue. This generates the KMIP PKI for your organization, creating the cryptographic foundation that will be used for secure KMIP communications.
This generates the KMIP PKI for your organization, creating the cryptographic foundation that will be used for secure KMIP communications.You do not need to manage these certificates yourself; Infisical handles the PKI infrastructure for you.
Create a Machine Identity for the KMIP Server
The KMIP server needs a machine identity to authenticate with Infisical and proxy requests on behalf of clients.Configure a machine identity by heading to your organization’s Access Control and switching over to the identities tab.
From there you can click Create Identity.This guide assumes you’ll be using the Universal Auth method for the machine identity but you can choose any supported authentication method. This machine identity will be used by the KMIP server to authenticate and forward client requests to Infisical KMS.
This machine identity will be used by the KMIP server to authenticate and forward client requests to Infisical KMS.
 This machine identity will be used by the KMIP server to authenticate and forward client requests to Infisical KMS.
This machine identity will be used by the KMIP server to authenticate and forward client requests to Infisical KMS.Create a Custom Organization Role with Proxy KMIP Permission
The machine identity needs permission to proxy KMIP requests.Create a custom organization role and give it the Proxy KMIP permission.
 This permission allows the KMIP server to act as an intermediary between KMIP clients and Infisical.
This permission allows the KMIP server to act as an intermediary between KMIP clients and Infisical.

 This permission allows the KMIP server to act as an intermediary between KMIP clients and Infisical.
This permission allows the KMIP server to act as an intermediary between KMIP clients and Infisical.Assign the Organization Role to the Machine Identity
Now connect the machine identity to the role you just created.Assign the machine identity to the custom organization role.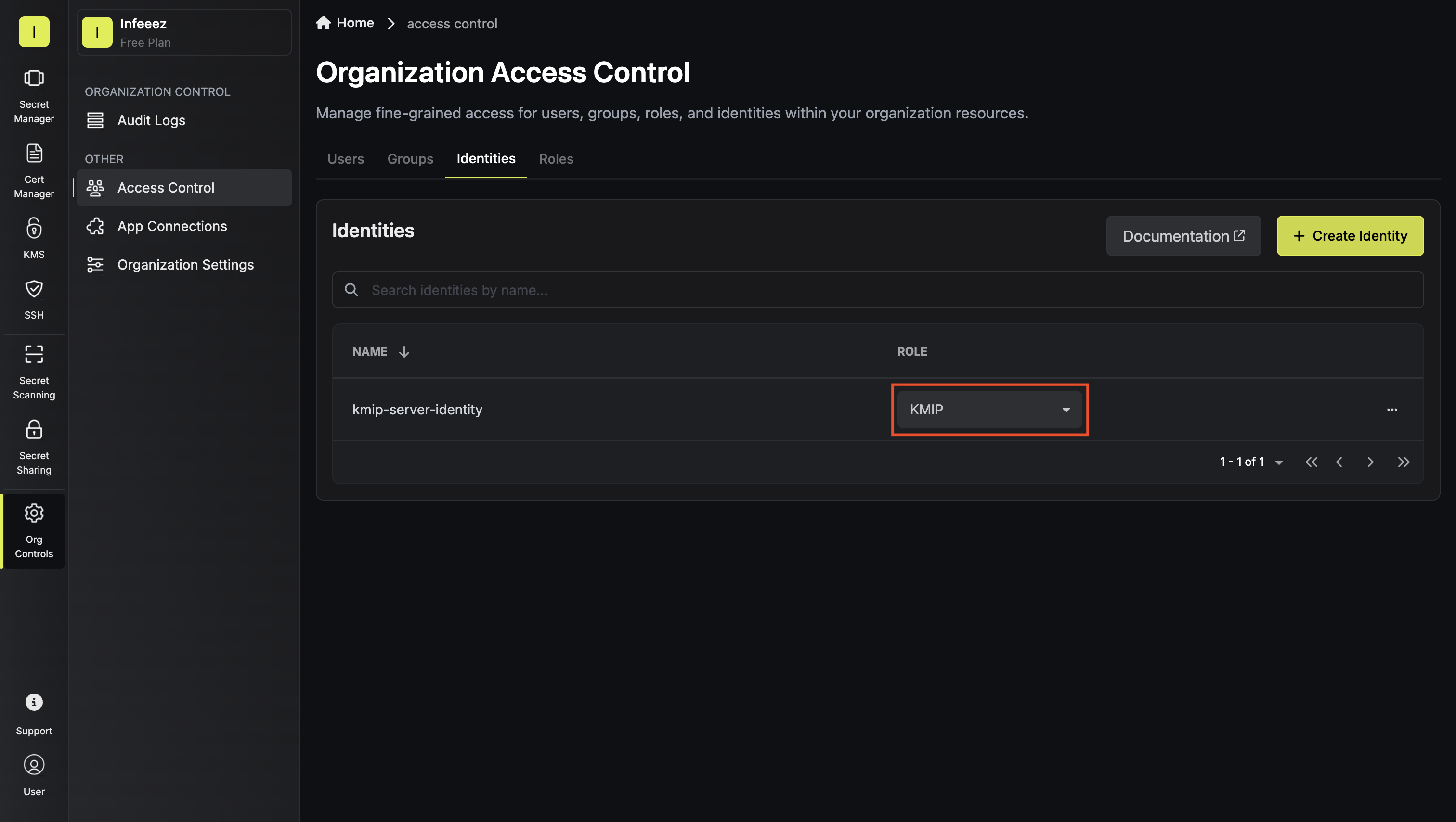 This grants the machine identity the ability to serve KMIP client requests and forward them from your KMIP server to Infisical.
This grants the machine identity the ability to serve KMIP client requests and forward them from your KMIP server to Infisical.
 This grants the machine identity the ability to serve KMIP client requests and forward them from your KMIP server to Infisical.
This grants the machine identity the ability to serve KMIP client requests and forward them from your KMIP server to Infisical.Deploy the KMIP Server
Now you’re ready to deploy the KMIP server.
You can run the KMIP server on any infrastructure that can reach the Infisical platform, such as a VM or container.Once you have your infrastructure ready, you’ll need to install the Infisical CLI on the server where you want to run the KMIP server.To install the latest Infisical CLI visit Infisical CLI instructions.
If you need to install specific versions of the CLI, you can find them on the Infisical CLI GitHub Releases.Then, launch the KMIP server with the following command:Available flags:
- listen-address (default: localhost:5696): The address the KMIP server listens on. In most cases you’ll want to listen on all interfaces (0.0.0.0:5696)
- identity-auth-method (default: universal-auth): The authentication method for the machine identity
- identity-client-id: The client ID of the machine identity (can be set via
INFISICAL_UNIVERSAL_AUTH_CLIENT_IDenv var) - identity-client-secret: The client secret of the machine identity (can be set via
INFISICAL_UNIVERSAL_AUTH_CLIENT_SECRETenv var) - server-name (default: “kmip-server”): The name of the KMIP server
- certificate-ttl (default: “1y”): The duration for which the server certificate is valid
- hostnames-or-ips: The IP address or the hostname of the server where you have deployed the KMIP server.
Navigate to Your KMS Project
Now that the KMIP server is running, you need to register KMIP clients that will connect to it.Navigate to the desired KMS project if you already have one or create a new project of type KMS, then select KMIP once inside the project, and click Add KMIP Client.

Configure the KMIP Client
Define the client and its permissions.In the modal, provide the details of your client. The selected permissions determine what KMIP operations (Create, Get, Revoke, etc.) can be performed in your KMS project.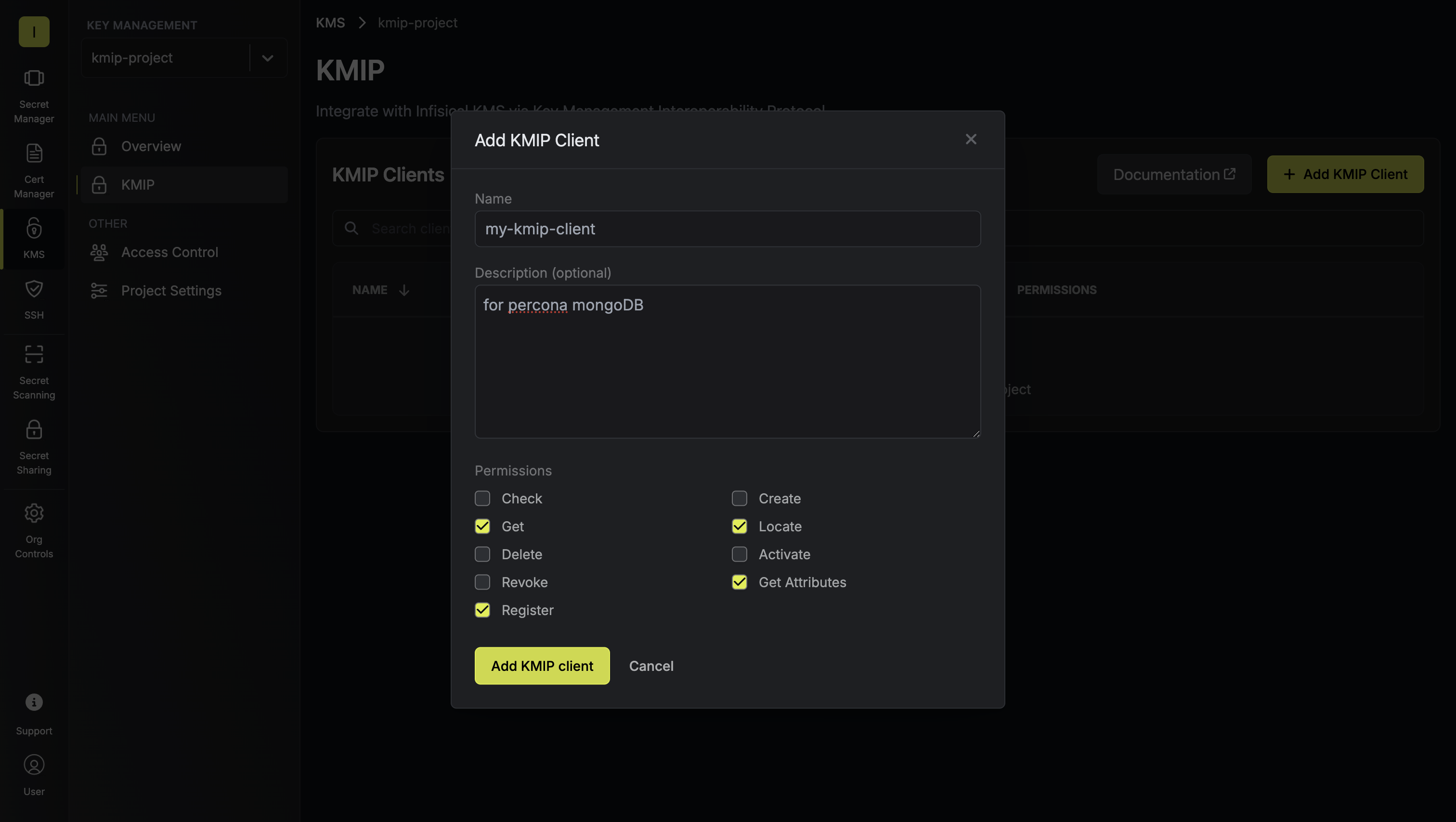 This creates a KMIP client entity in Infisical that will be authenticated via mTLS certificates.
This creates a KMIP client entity in Infisical that will be authenticated via mTLS certificates.
 This creates a KMIP client entity in Infisical that will be authenticated via mTLS certificates.
This creates a KMIP client entity in Infisical that will be authenticated via mTLS certificates.Generate Client Certificate
Each KMIP client needs its own certificate for mTLS authentication.Click Generate Certificate for your newly created client.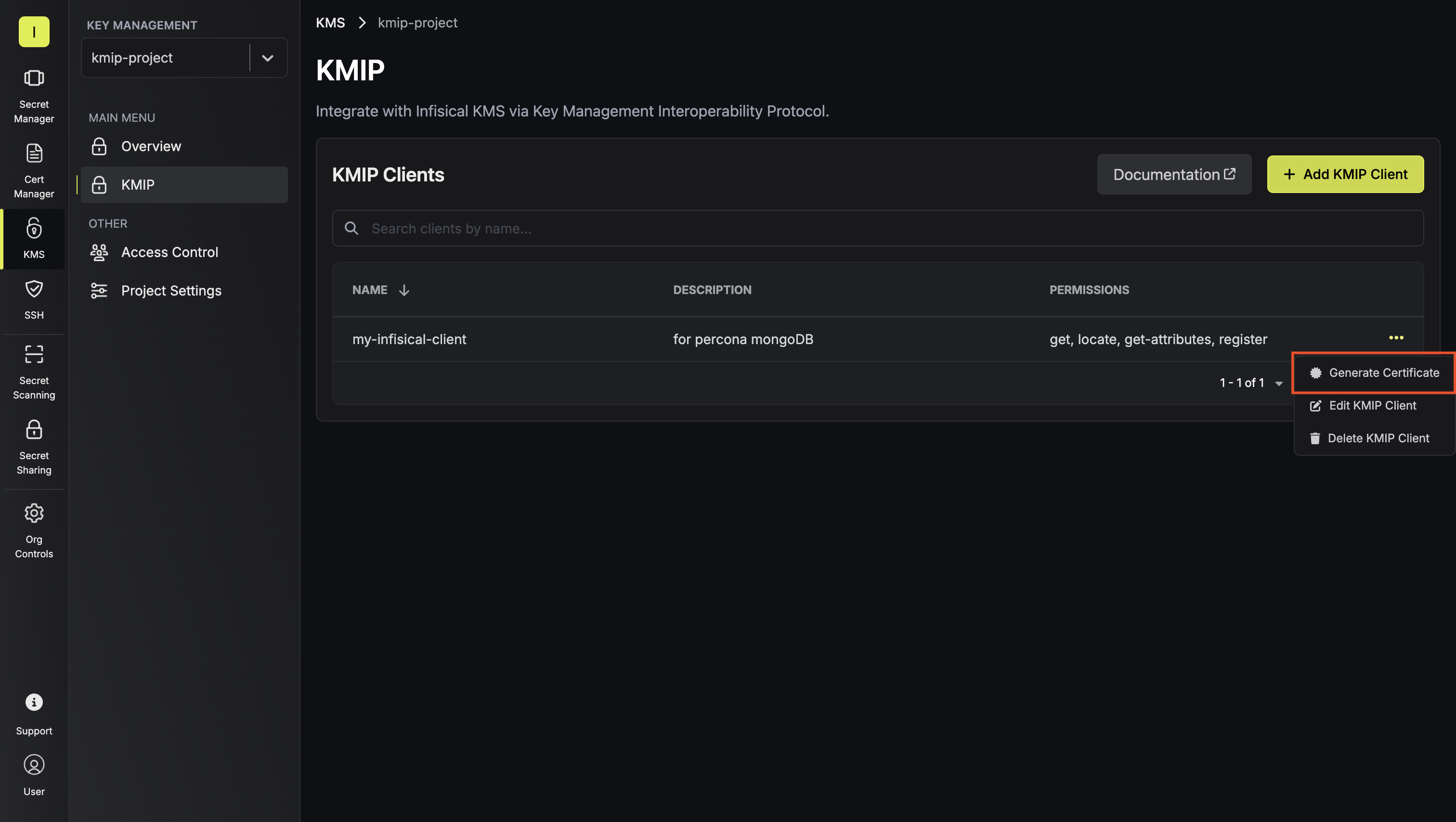 Provide the desired TTL (time-to-live) and key algorithm, then click Generate Client Certificate.
Provide the desired TTL (time-to-live) and key algorithm, then click Generate Client Certificate.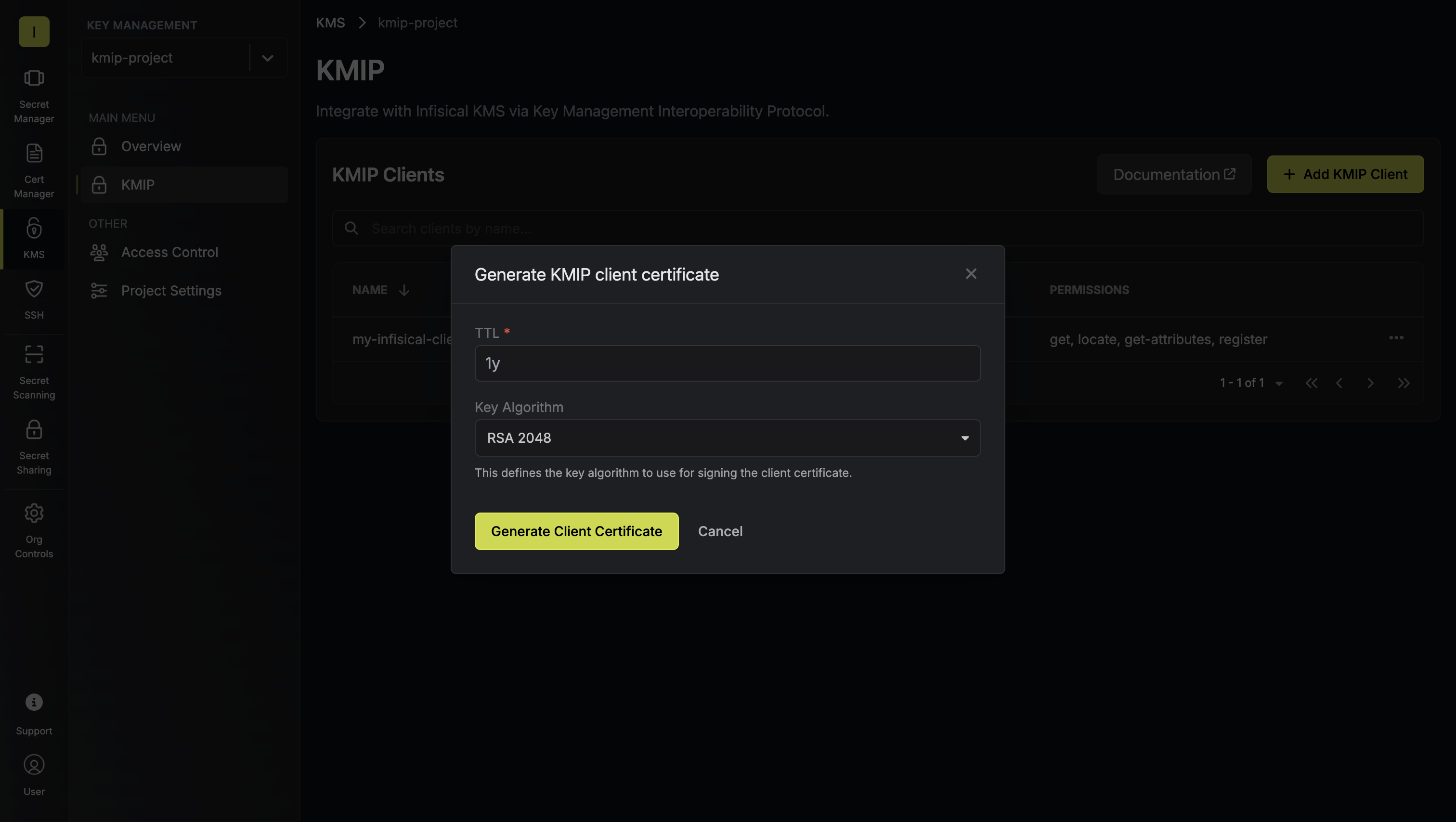 Download the generated client certificate, certificate chain, and private key.
Download the generated client certificate, certificate chain, and private key.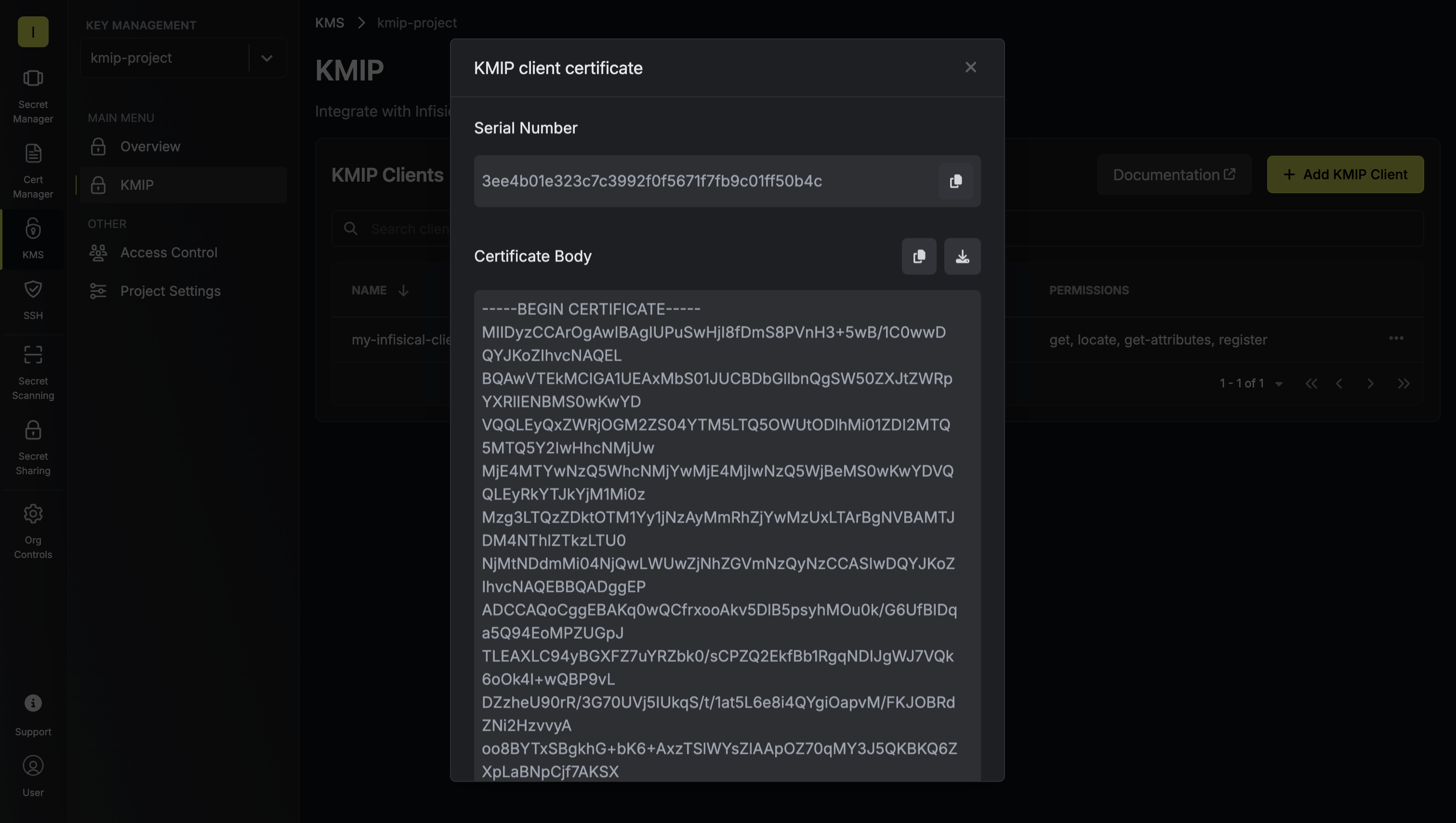 Configure your KMIP-compatible applications or tools to use these credentials when connecting to the KMIP server. The client will now authenticate via mTLS and perform authorized key management operations through the KMIP server, which proxies requests to Infisical KMS.
Configure your KMIP-compatible applications or tools to use these credentials when connecting to the KMIP server. The client will now authenticate via mTLS and perform authorized key management operations through the KMIP server, which proxies requests to Infisical KMS.
 Provide the desired TTL (time-to-live) and key algorithm, then click Generate Client Certificate.
Provide the desired TTL (time-to-live) and key algorithm, then click Generate Client Certificate. Download the generated client certificate, certificate chain, and private key.
Download the generated client certificate, certificate chain, and private key. Configure your KMIP-compatible applications or tools to use these credentials when connecting to the KMIP server. The client will now authenticate via mTLS and perform authorized key management operations through the KMIP server, which proxies requests to Infisical KMS.
Configure your KMIP-compatible applications or tools to use these credentials when connecting to the KMIP server. The client will now authenticate via mTLS and perform authorized key management operations through the KMIP server, which proxies requests to Infisical KMS.Connecting your KMIP Client to Infisical
After completing the setup, configure your KMIP compatible application to connect to the KMIP server. While exact configuration steps vary by application, you’ll generally need to provide:-
KMIP Server Address: The hostname or IP and port where your KMIP server is listening (e.g.,
my-kmip-server.com:5696) -
Client Certificates: The certificate credentials generated from your Infisical KMS project:
- Client Certificate (
client-cert.pem) - Identifies your KMIP client - Client Private Key (
client-key.pem) - Used for mTLS authentication - Certificate Chain (
cert-chain.pem) - Verifies the KMIP server
- Client Certificate (
General Configuration Steps
Identify Your KMIP Server Endpoint
Determine the address where your KMIP server is accessible. This should match one of the hostnames or IPs you specified when starting the KMIP server with the
--hostnames-or-ips flag.Example endpoints:my-kmip-server.com:569610.0.1.50:5696kmip.example.com:5696
5696, but this can be changed using the --listen-address flag when starting the server.Prepare Certificate Files
Organize the certificate materials you downloaded when generating the client certificate from the Infisical KMS project. You should have three files:
- client-cert.pem - The client certificate
- cert-chain.pem - The certificate chain (includes intermediate and root CA certificates)
- client-key.pem - The private key
Configure Your KMIP Client Application
The exact configuration steps vary depending on your KMIP client application. Generally, you’ll need to specify:Common configuration parameters:
- Server hostname/IP: Your KMIP server address (e.g.,
my-kmip-server.com) - Server port: Default is
5696 - Client certificate: Path to
client-cert.pem - Client private key: Path to
client-key.pem - CA certificate: Path to
cert-chain.pem(used to verify the server) - Protocol version: KMIP 1.0 through 1.4 are supported
Test the Connection
Once configured, test the connection by performing a simple KMIP operation, such as:This command attempts to establish a TLS connection to the KMIP server using your client certificate and key, displaying detailed information about the handshake process.
If the connection is successful, you’ll see the server’s certificate chain and a message indicating that the handshake was completed.
- Querying server capabilities
- Creating a test key
- Listing available keys
- Verify network connectivity between your KMIP client and the KMIP server
- Check that certificate files are readable and in the correct format
- Ensure the KMIP server is running and accessible
- Review KMIP server logs for authentication errors
- Confirm the client certificate has not expired

