- KV v1 and KV v2 secrets
- Kubernetes auth method configurations (become Machine Identities in Infisical)
- Kubernetes secrets engine roles (become Dynamic Secrets in Infisical)
- Vault policies (translated to Infisical project roles)
Set Up Your Vault Connection
Before importing anything, you need to establish a secure connection between Infisical and your Vault instance. This is a one-time setup.Create a Vault policy
In your Vault instance, create a policy that allows Infisical to read your secrets, policies, and authentication configurations. This policy grants read-only access and doesn’t allow Infisical to modify or create resources within your Vault instance.
Save this policy in Vault with the name
View the complete policy
View the complete policy
infisical-in-platform-migration.Create an App Connection in Infisical
In Infisical, navigate to Organization Settings > App Connections and create a new HashiCorp Vault connection.Follow the HashiCorp Vault App Connection documentation for detailed setup instructions. When configuring authentication (Token or AppRole), make sure it uses the
infisical-in-platform-migration policy you created.Add Vault Namespaces for Migration
Navigate to Organization Settings > External Migrations in Infisical.Under the “In-Platform Migration Tooling” section for HashiCorp Vault, click ”+ Add Namespace”.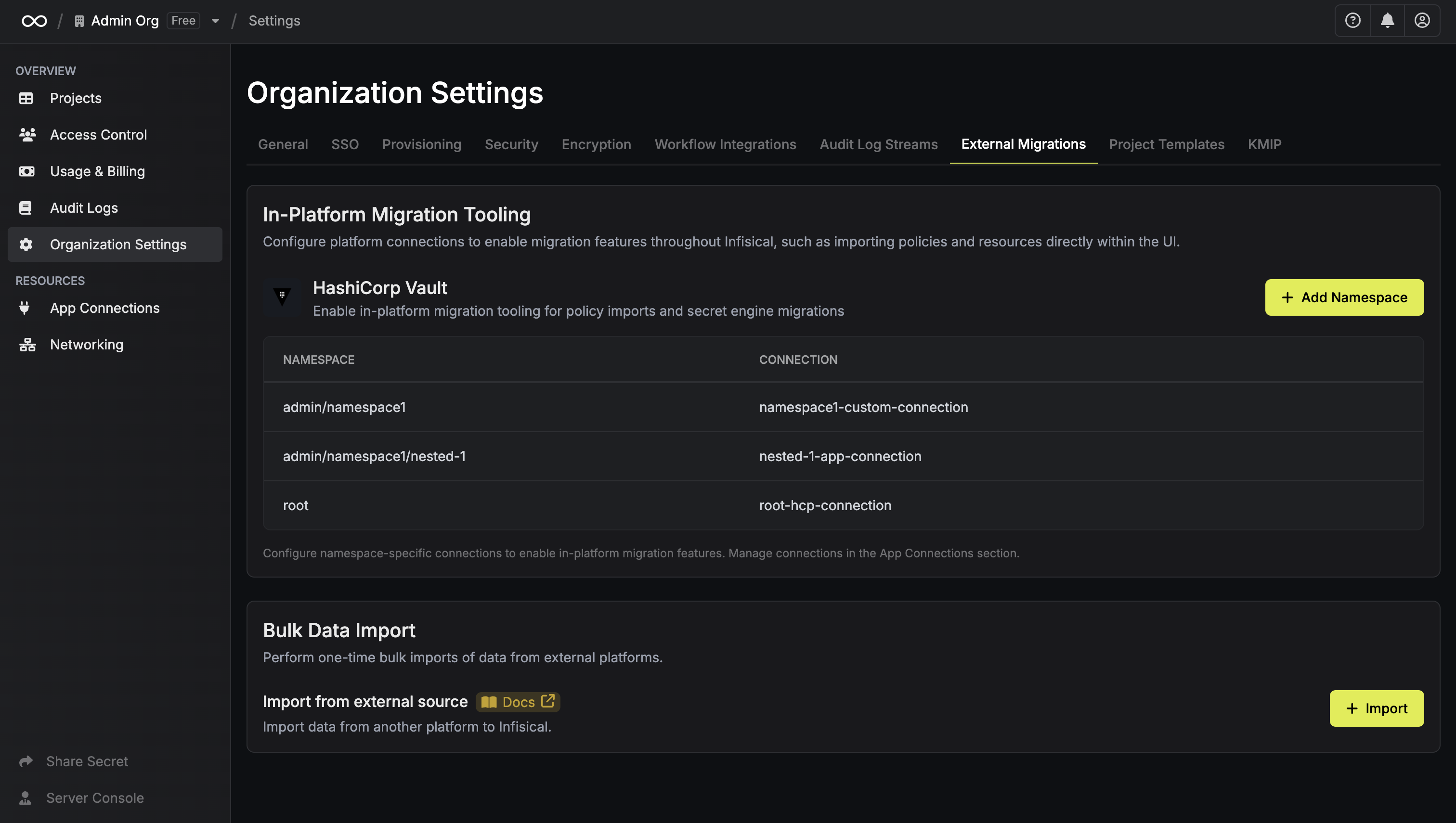 Configure your namespace:
Configure your namespace: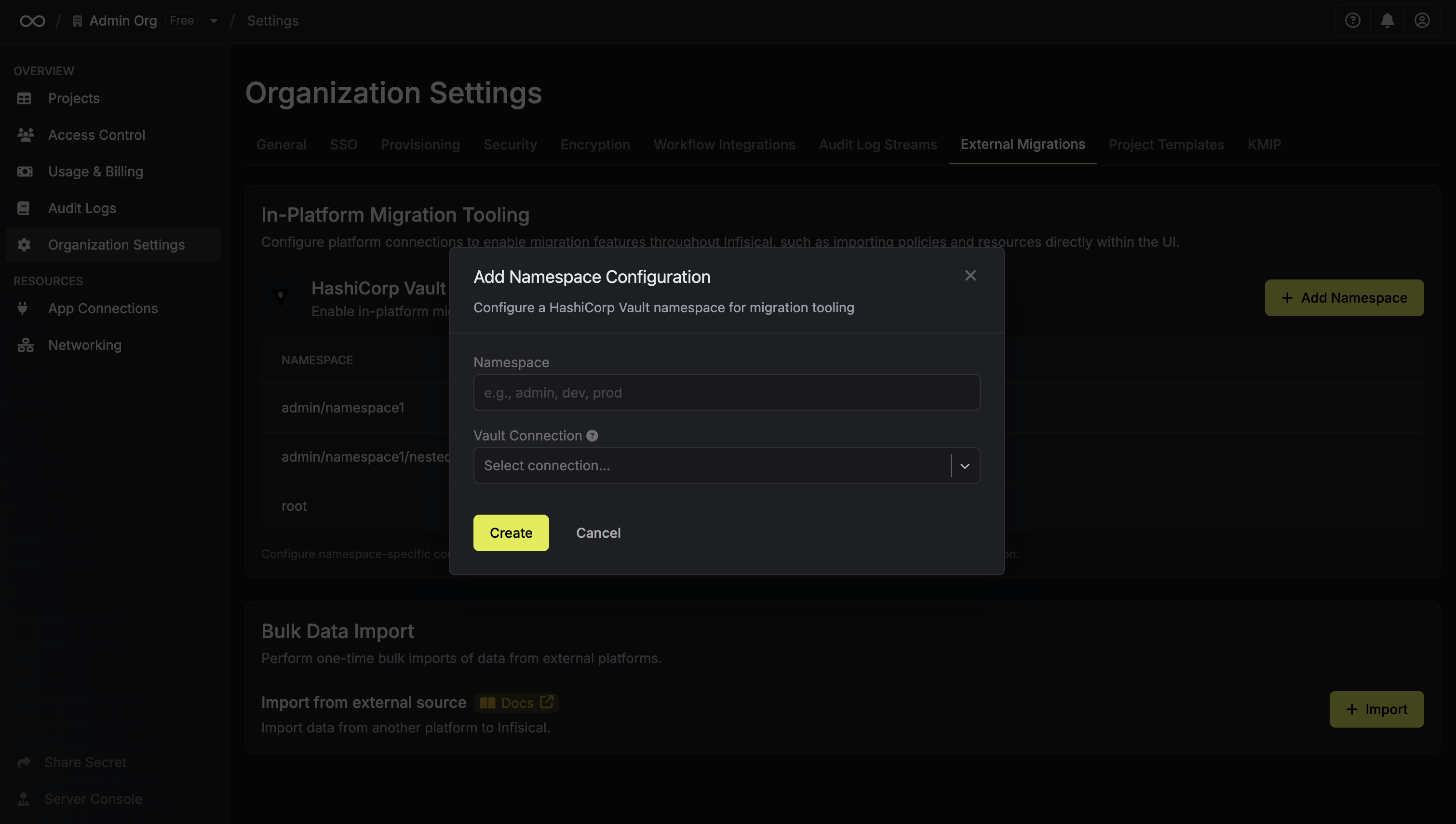
 Configure your namespace:
Configure your namespace:
- Namespace: Enter your Vault namespace path (e.g.,
admin/namespace1). If you intend to use the root namespace, set the namespace value to “root”. - Connection: Select the App Connection you created in the previous step.
You can add multiple namespaces with different connections if you have multiple Vault instances or namespaces to migrate from.
Migrate Your Resources
Once your Vault connection is configured, you’ll see import options throughout Infisical wherever relevant. The sections below cover each type of resource you can migrate.Migrating KV Secrets
KV secrets are imported into a specific environment (e.g., Development, Staging, Production) within a project. If you’re coming from Vault, think of a project as similar to a KV secret engine dedicated to one application.First time? You’ll need to create a project first. A project in Infisical typically represents a single application or microservice.
- Navigate to your project and select a specific environment (e.g., Development, Production)
-
In the secrets view, click the dropdown icon (caret) next to the ”+ Add Secret” button
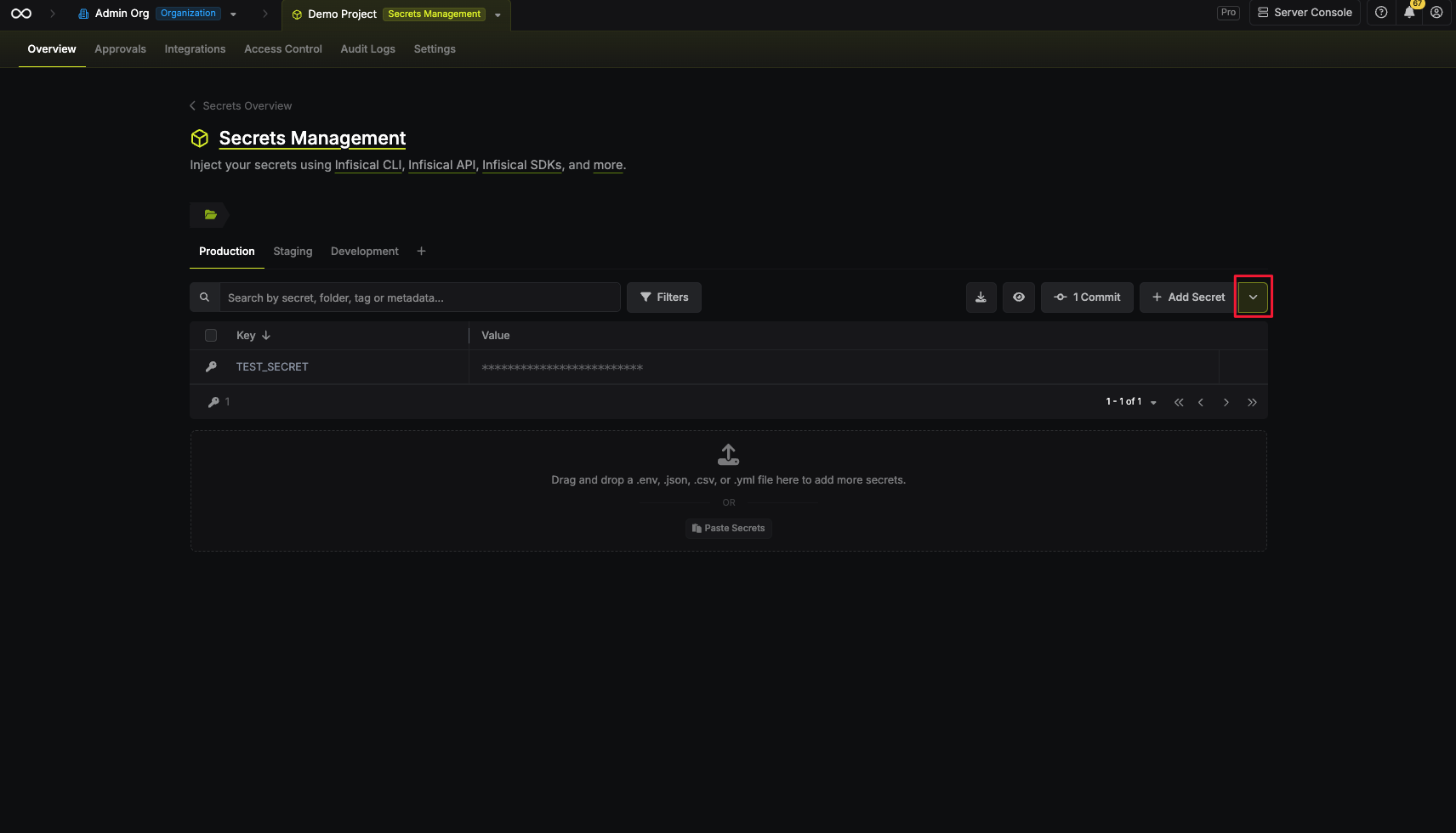
-
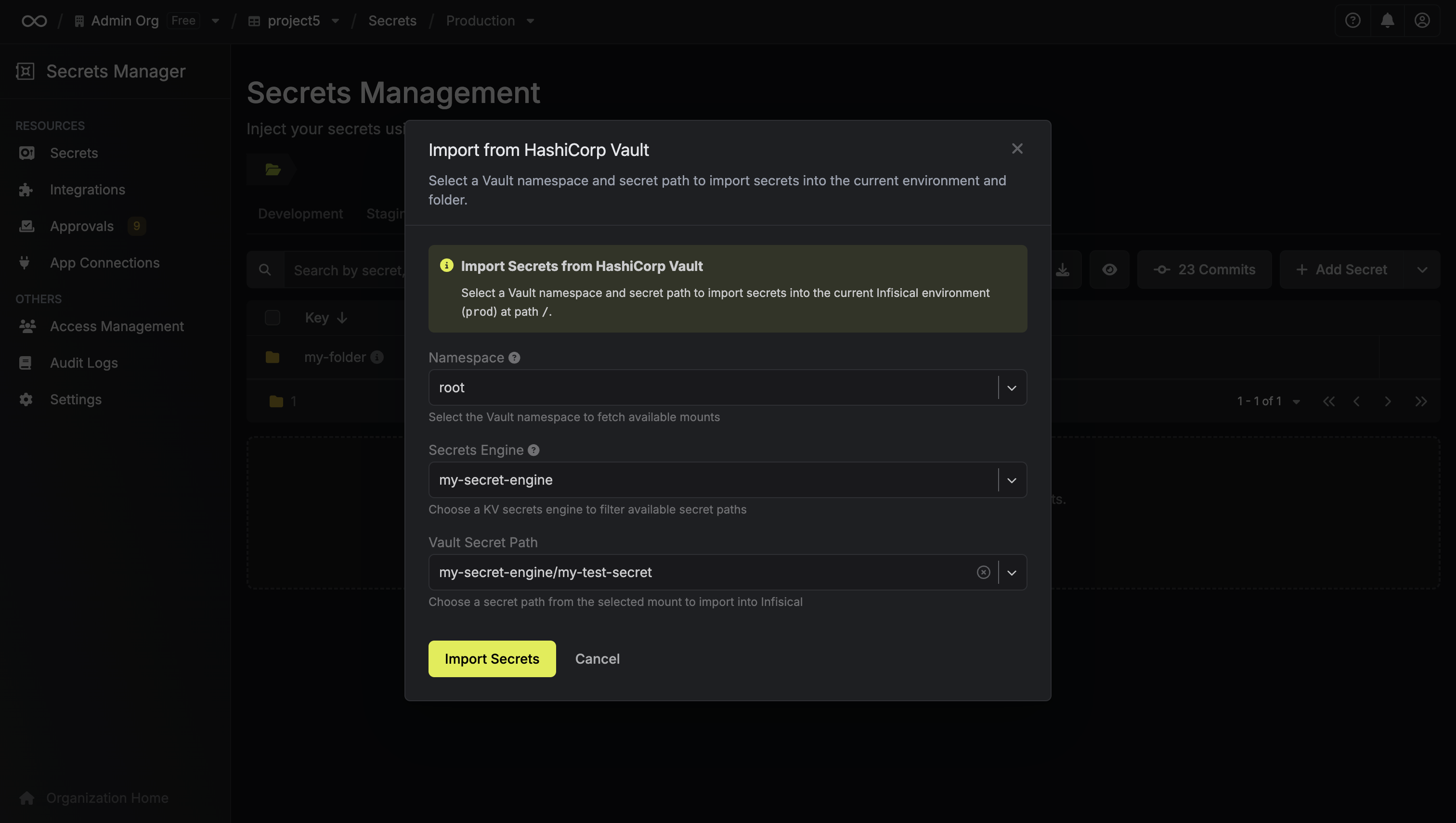
Select “Add from HashiCorp Vault”
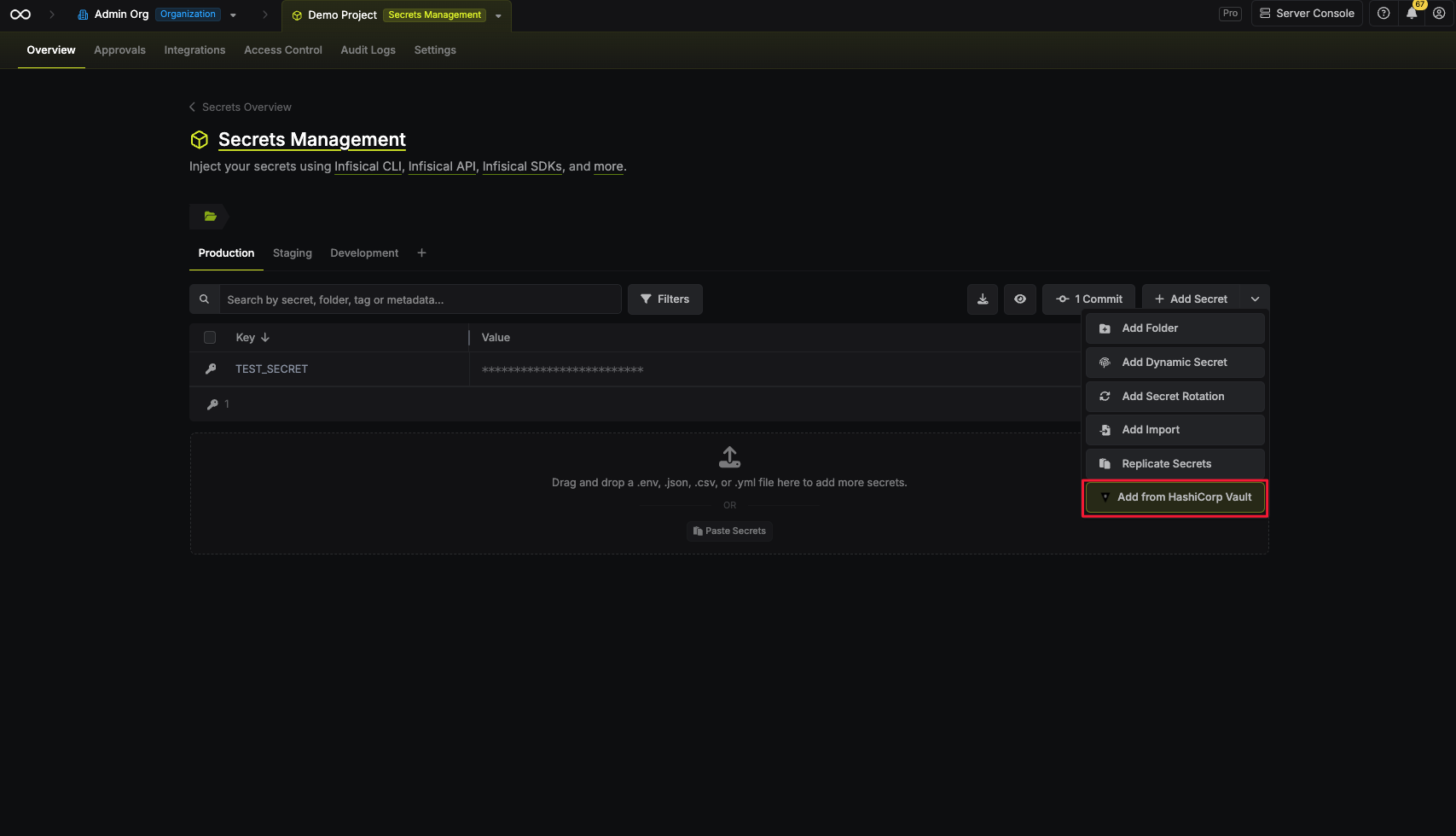
-
Choose your Vault namespace and the secret path you want to import (e.g.,
secret/app/prod) -
Click “Import Secrets”
Migrating Kubernetes Auth Method
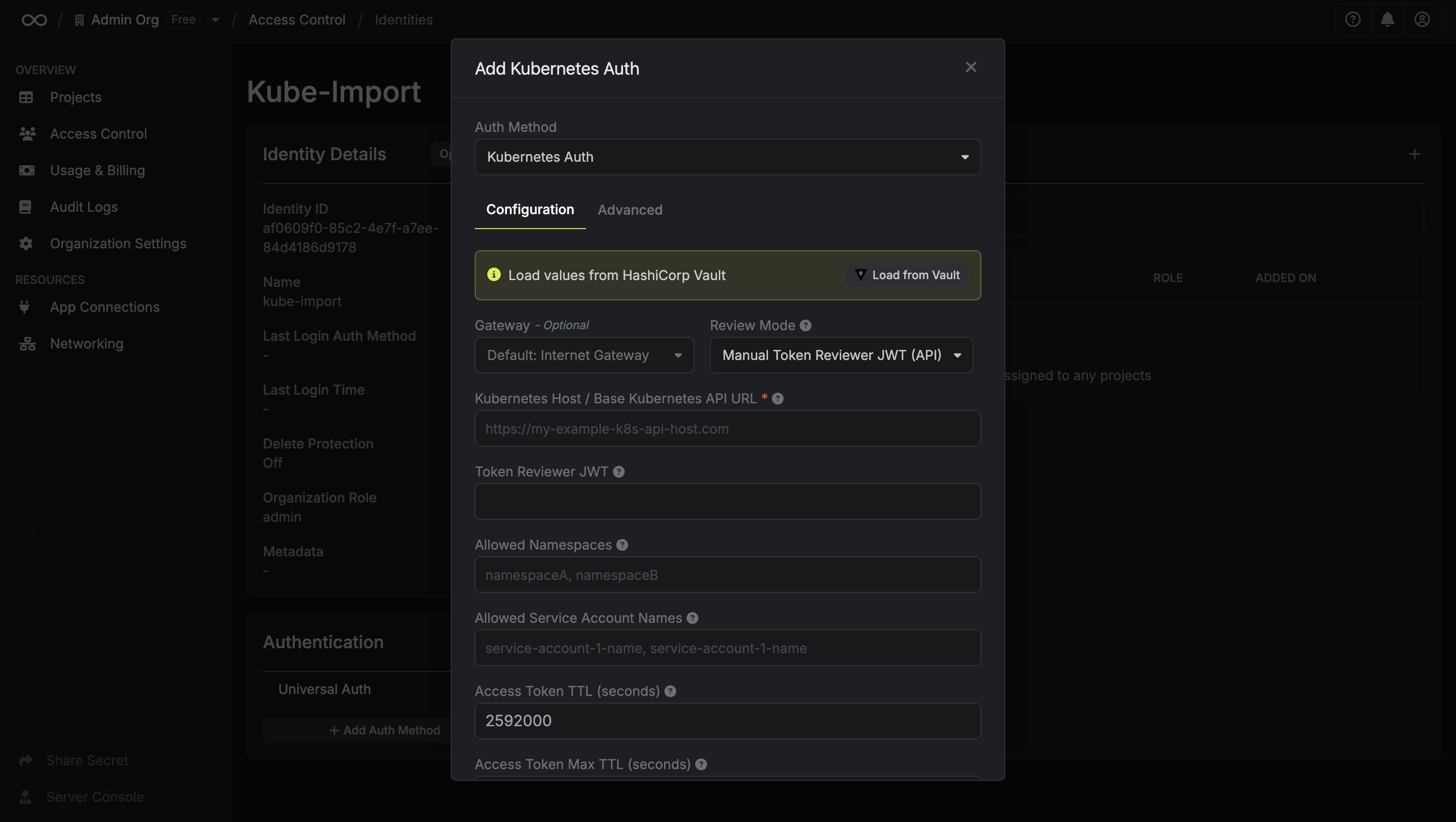
If you’re using Vault’s Kubernetes auth method to authenticate your pods, you can migrate this configuration to Infisical’s Machine Identities. In Vault, you define Kubernetes roles that specify which service accounts can authenticate. In Infisical, this maps to a Machine Identity with Kubernetes authentication enabled. To import Kubernetes auth configuration:- First, create a Machine Identity in Infisical
- Navigate to Access Control > Machine Identities and select the identity
- Click “Add Authentication Method” and choose Kubernetes Auth
-
In the configuration modal, click “Load from Vault”
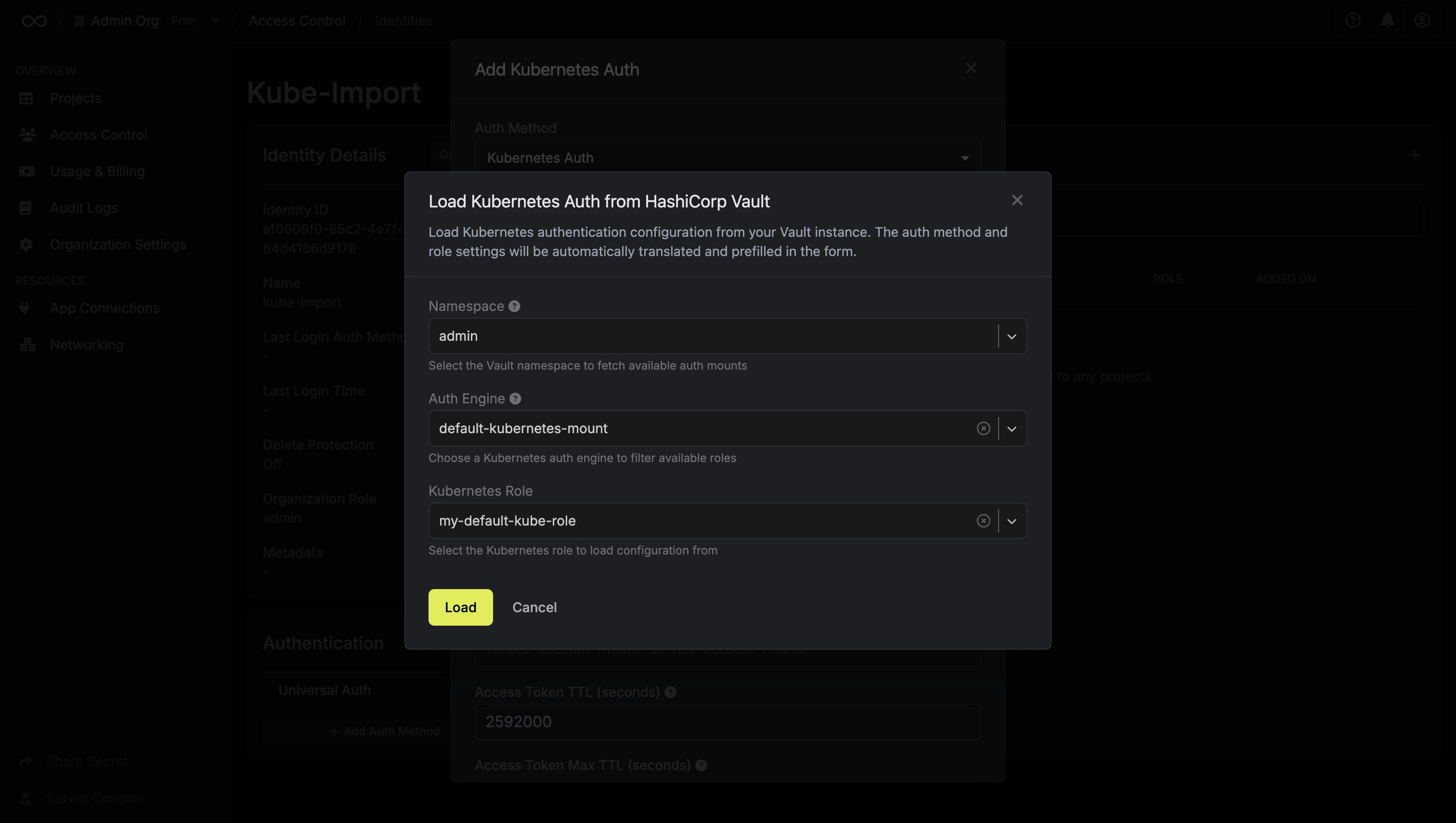
- Select your Vault namespace and the Kubernetes role
-
Click “Load”
Sensitive values like service account JWTs cannot be retrieved from Vault and
must be manually provided in the form after importing the configuration.
Migrating Kubernetes Secrets Engine Roles
If you’re using Vault’s Kubernetes secrets engine to generate short-lived Kubernetes credentials, you can migrate these roles to Infisical’s Dynamic Secrets. Both platforms support generating temporary Kubernetes service account tokens or creating temporary service accounts, so the configuration is similar. To import a Kubernetes dynamic secret configuration:- Navigate to your project and select an environment
- Click ”+ Add Secret” dropdown and choose “Dynamic Secret”
- Select Kubernetes as the provider
-
Click “Load from Vault” at the top of the form
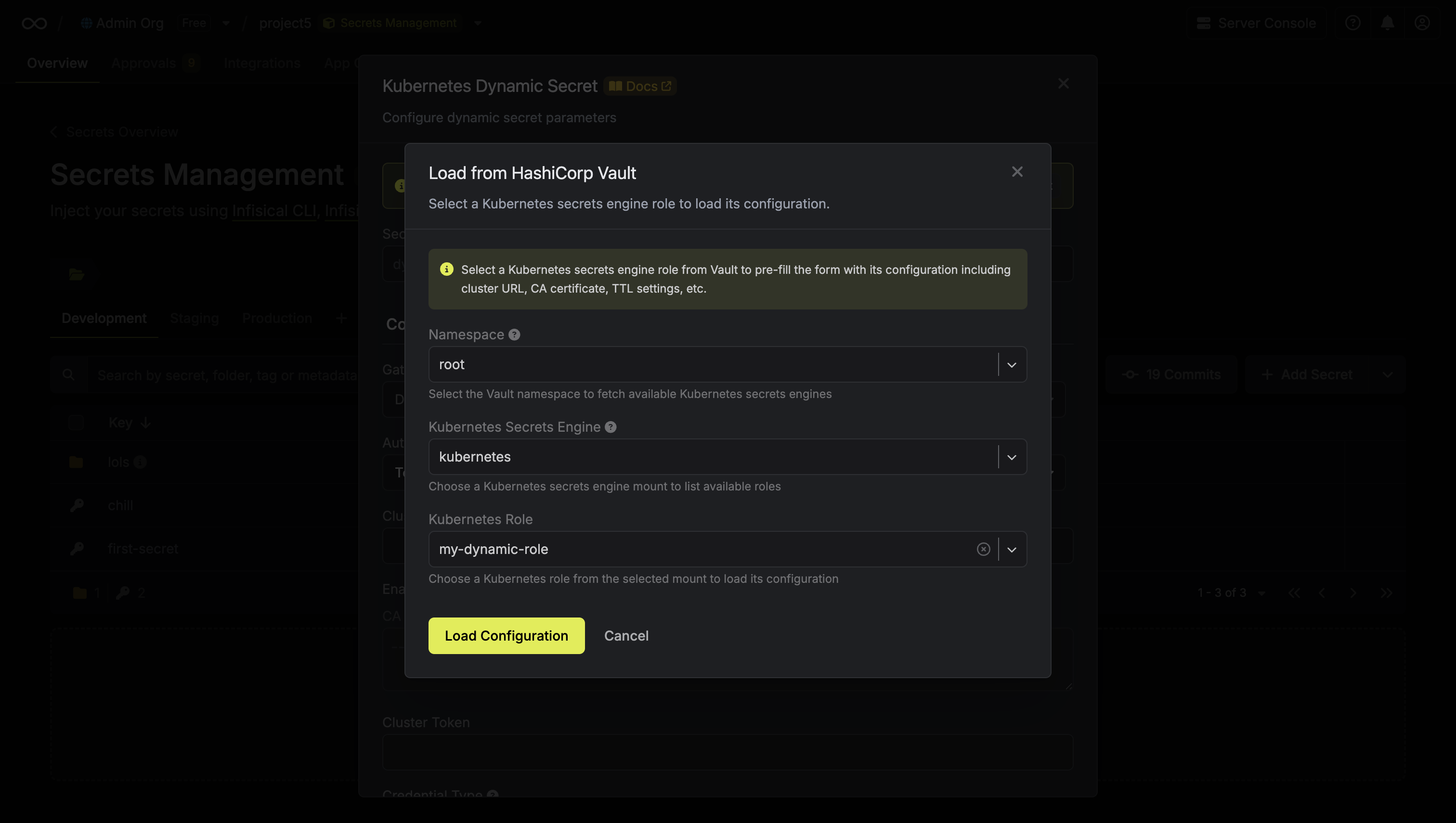
- Select your Vault namespace, Kubernetes secrets engine mount, and role
- Click “Load Configuration”
- Cluster URL and CA certificate
- Credential type (Static or Dynamic)
- Service account name or Kubernetes role settings
- Allowed namespaces
- Token TTL values
- Token audiences
Sensitive values like cluster tokens cannot be retrieved from Vault and must
be manually provided in the form after loading the configuration.
Migrating Vault Policies
Infisical can translate your Vault HCL policies into Infisical project roles. The table below shows how Vault capabilities map to Infisical permissions:| Vault Capability | Infisical Permission |
|---|---|
read | Read secrets |
list | Read secrets (list is implicit with read) |
create | Create secrets |
update | Edit secrets |
delete | Delete secrets |
Policy translation is best-effort and provides a starting point based on your
Vault configuration. The translated permissions should be reviewed and
adjusted as needed since Vault and Infisical have different access control
models.
- Navigate to your project, then go to Access Control > Roles and create or edit a role
-
In the policy configuration, click “Add from HashiCorp Vault”
- Select your Vault namespace
-
Either choose an existing policy from the dropdown or paste your own HCL policy
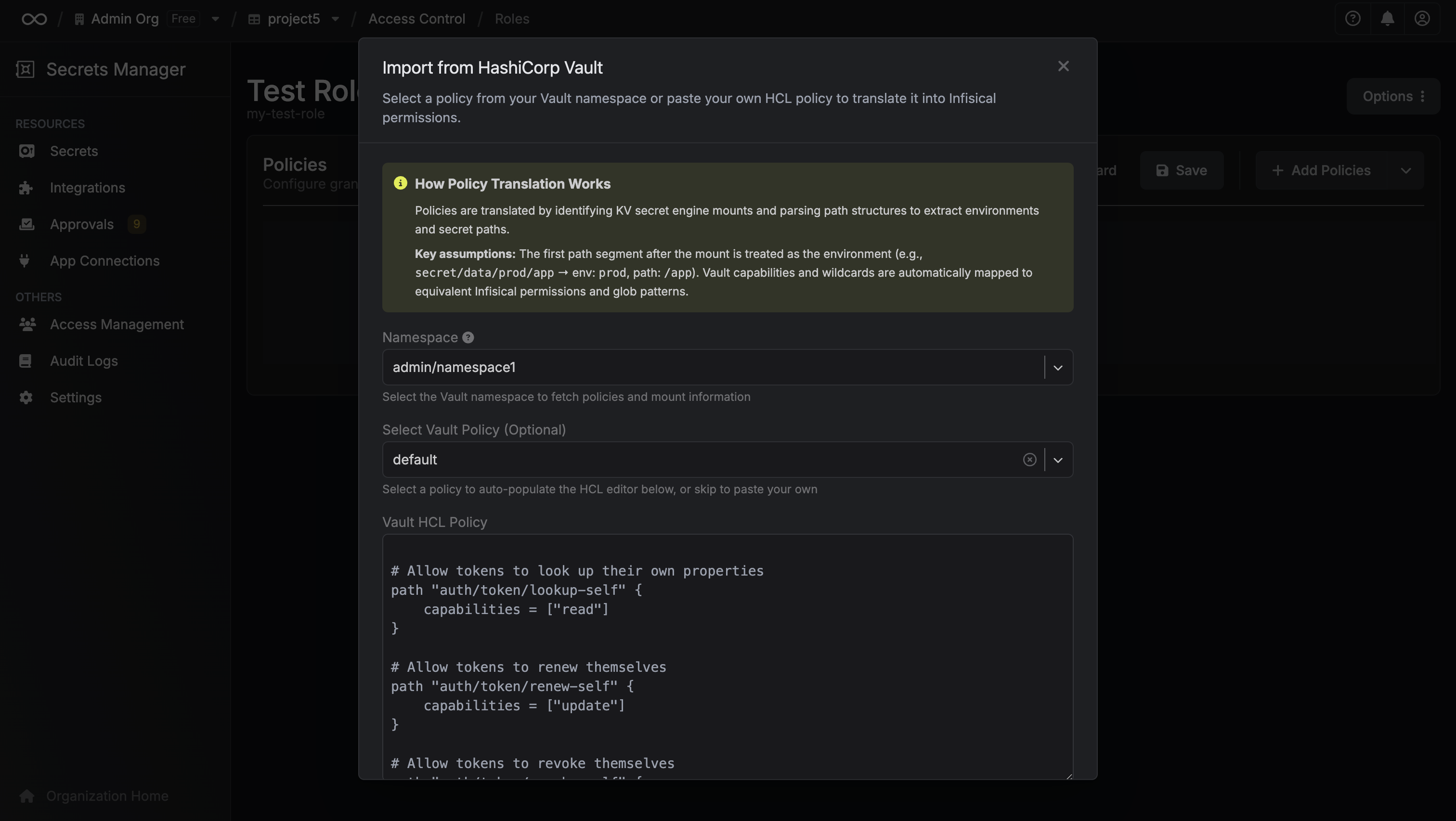
- Review the automatically translated Infisical permissions
- Make any adjustments and save

