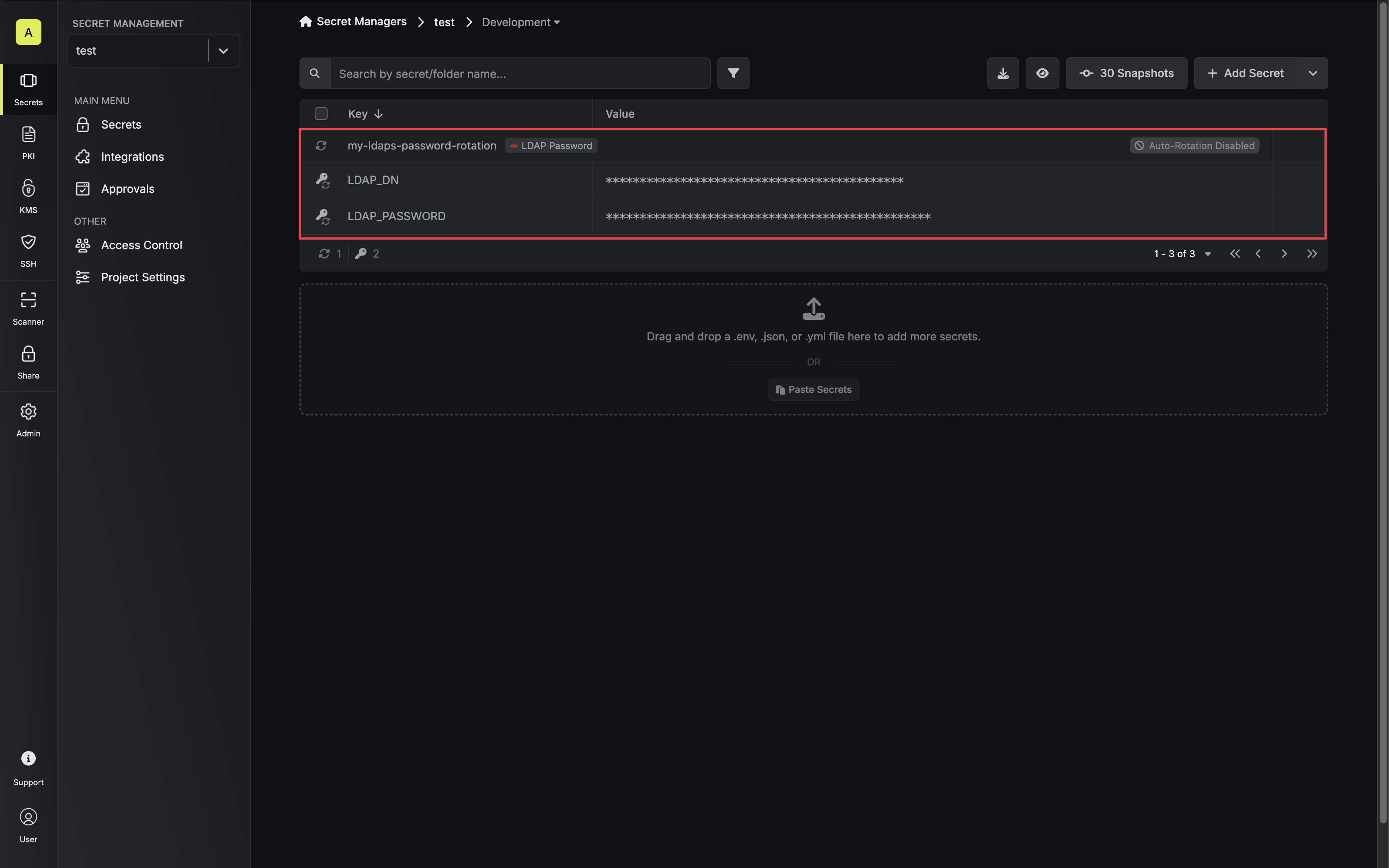
Due to how LDAP passwords are rotated, retired credentials will not be able to
authenticate with the LDAP provider during their inactive period.This is a limitation of the LDAP provider and cannot be
rectified by Infisical.
Prerequisites
- Create an LDAP Connection with the Secret Rotation requirements
- Ensure your network security policies allow incoming requests from Infisical to this rotation provider, if network restrictions apply.
Create an LDAP Password Rotation in Infisical
- Infisical UI
- API
-
Navigate to your Secret Manager Project’s Dashboard and select Add Secret Rotation from the actions dropdown.
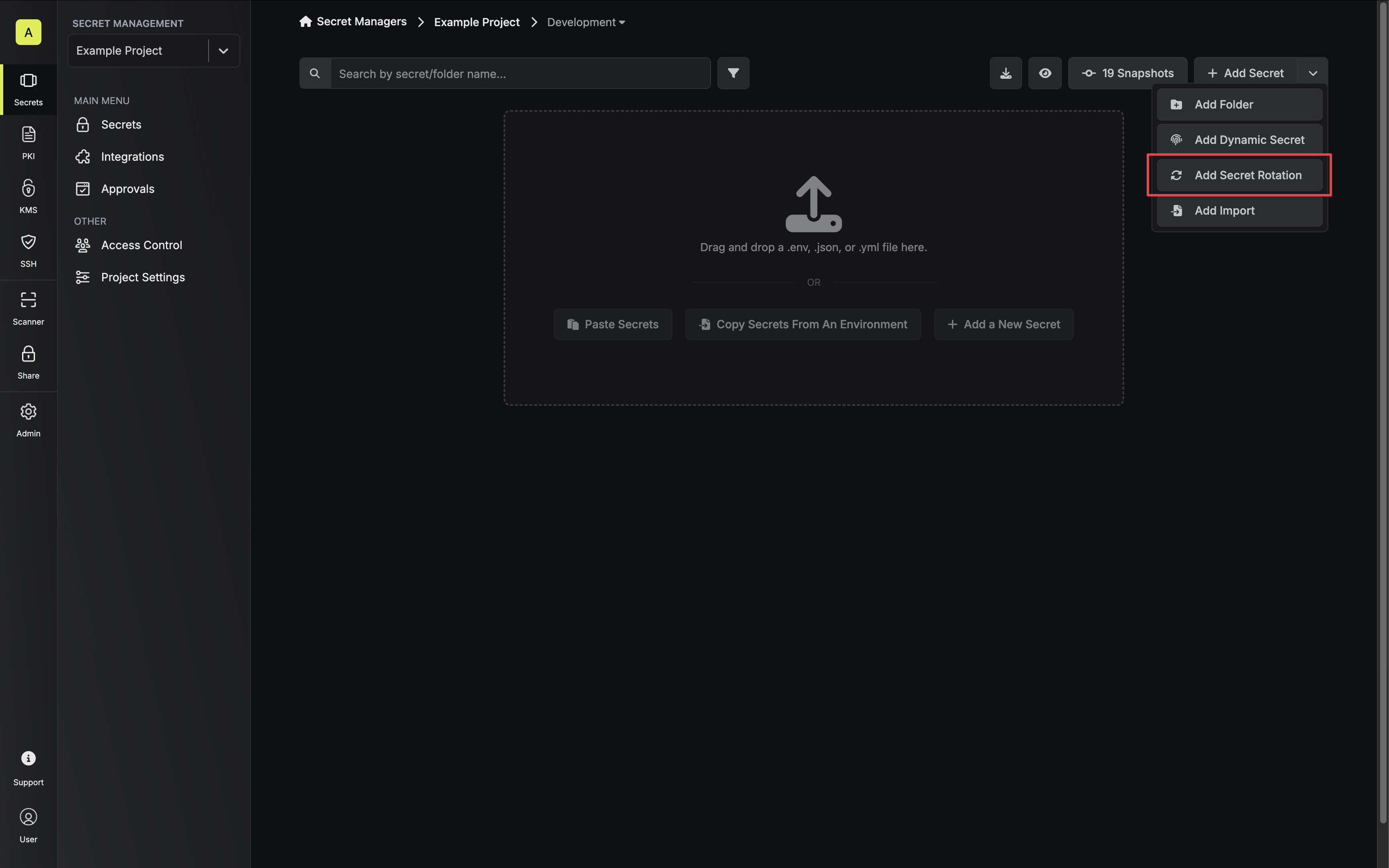
-
Select the LDAP Password option.
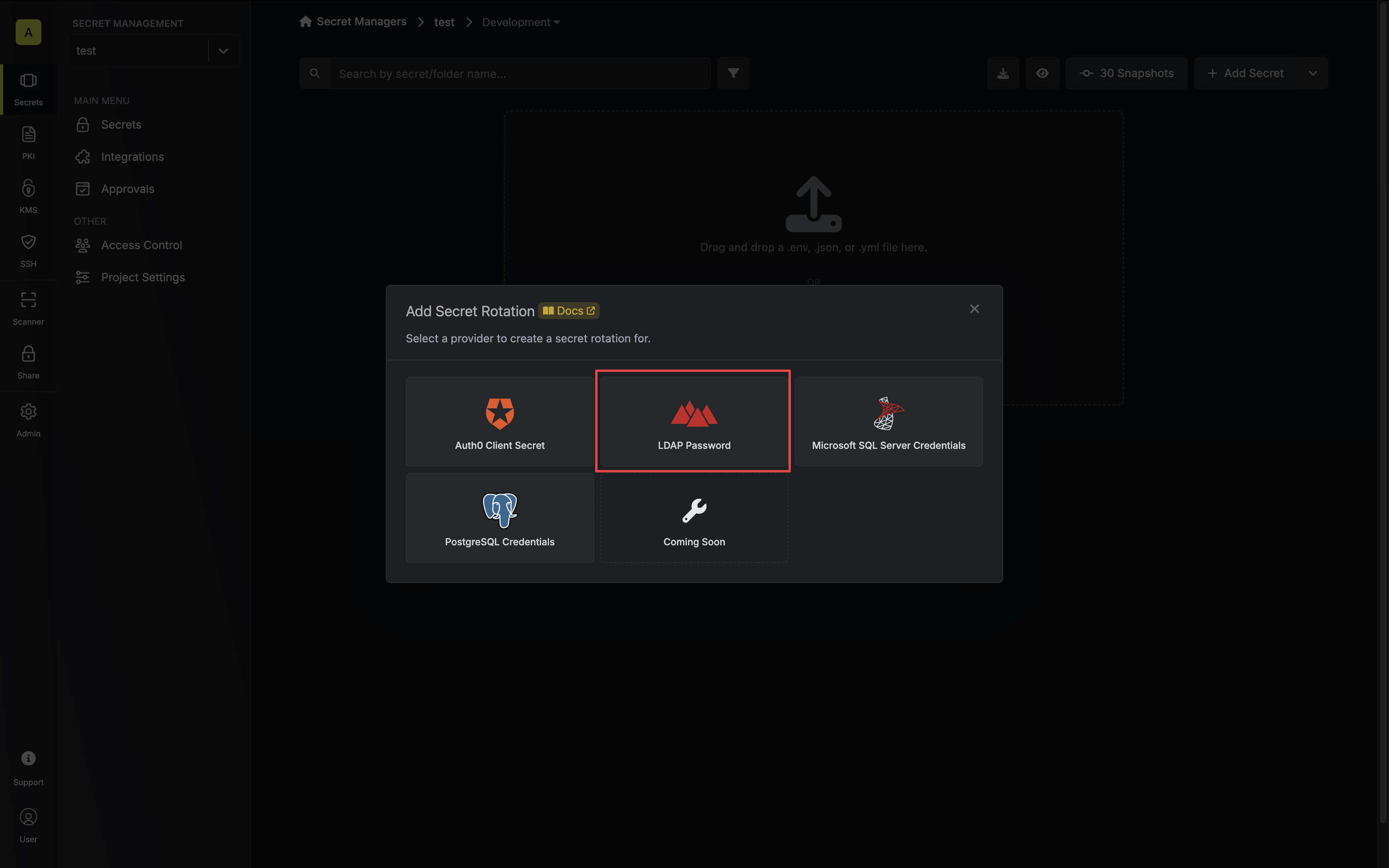
-
Select the LDAP Connection to use and configure the rotation behavior. Then click Next.
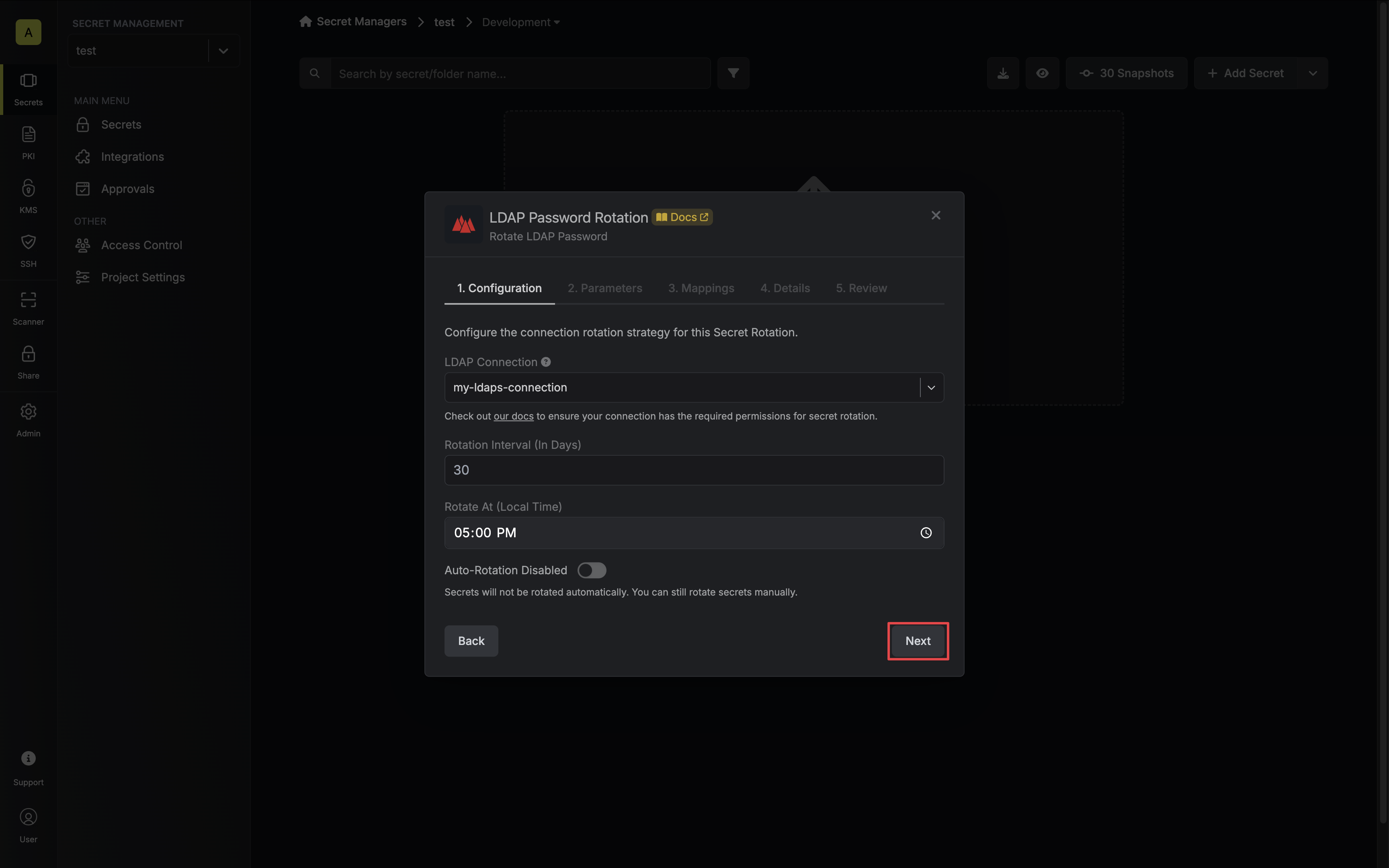
- LDAP Connection - the connection that will perform the rotation of the configured principal’s password.
LDAP Password Rotations require an LDAP Connection that uses ldaps:// protocol.- Rotation Interval - the interval, in days, that once elapsed will trigger a rotation.
- Rotate At - the local time of day when rotation should occur once the interval has elapsed.
- Auto-Rotation Enabled - whether secrets should automatically be rotated once the rotation interval has elapsed. Disable this option to manually rotate secrets or pause secret rotation.
Due to LDAP Password Rotations rotating a single credential set, auto-rotation may result in service interruptions. If you need to ensure service continuity, we recommend disabling this option. -
Configure the required Parameters for your rotation. Then click Next.
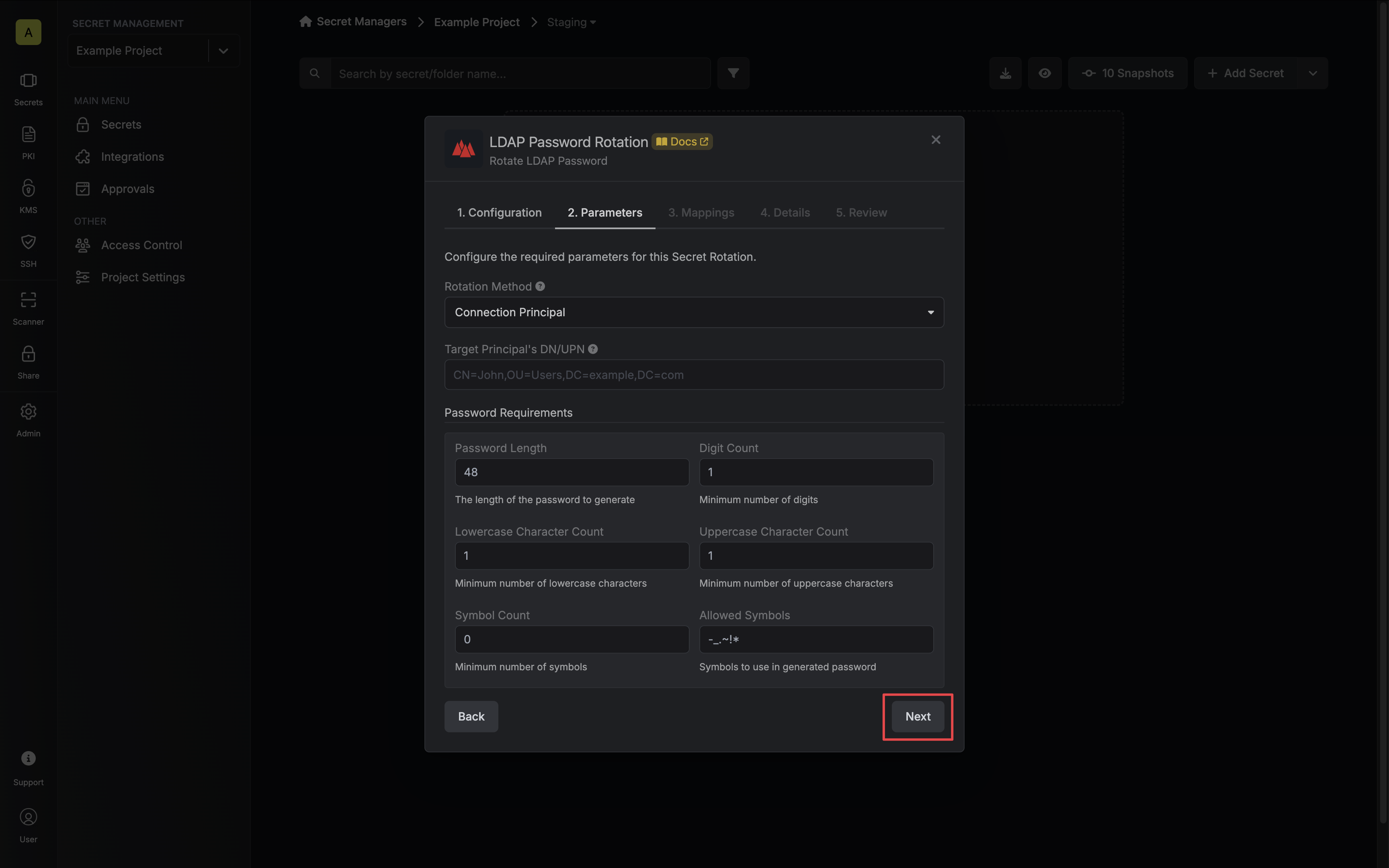
- Rotation Method - The method to use when rotating the target principal’s password.
- Connection Principal - Infisical will use the LDAP Connection’s binding principal to rotate the target principal’s password.
- Target Principal - Infisical will bind with the target Principal to rotate their own password.
- DN/UPN - The Distinguished Name (DN), or User Principal Name (UPN) if supported, of the principal whose password you want to rotate.
- Password - The target principal’s password (if Rotation Method is set to Target Principal).
- Password Requirements - The constraints to apply when generating new passwords.
-
Specify the secret names that the client credentials should be mapped to. Then click Next.
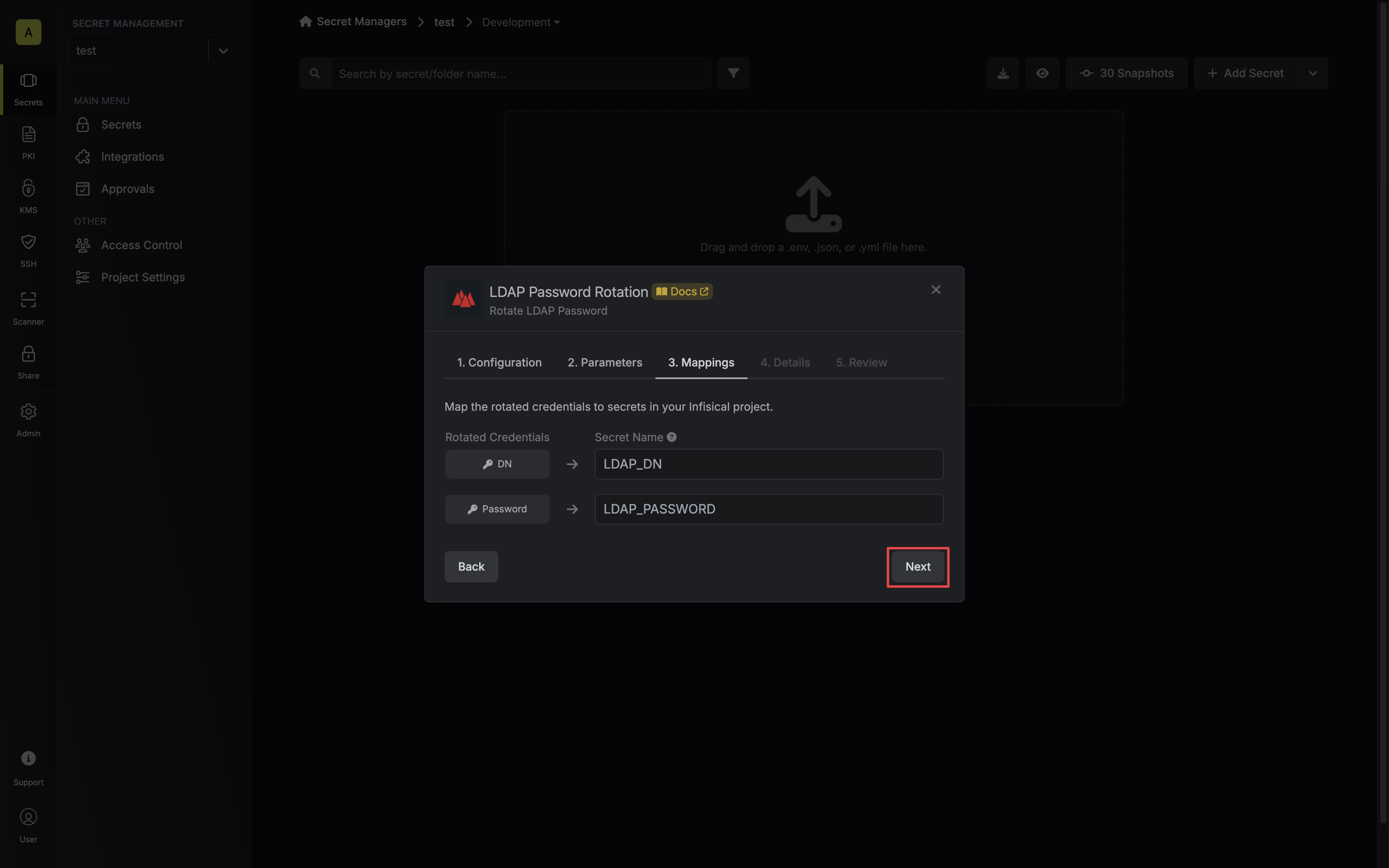
- DN/UPN - the name of the secret that the principal’s Distinguished Name (DN) or User Principal Name (UPN) will be mapped to.
- Password - the name of the secret that the rotated password will be mapped to.
-
Give your rotation a name and description (optional). Then click Next.
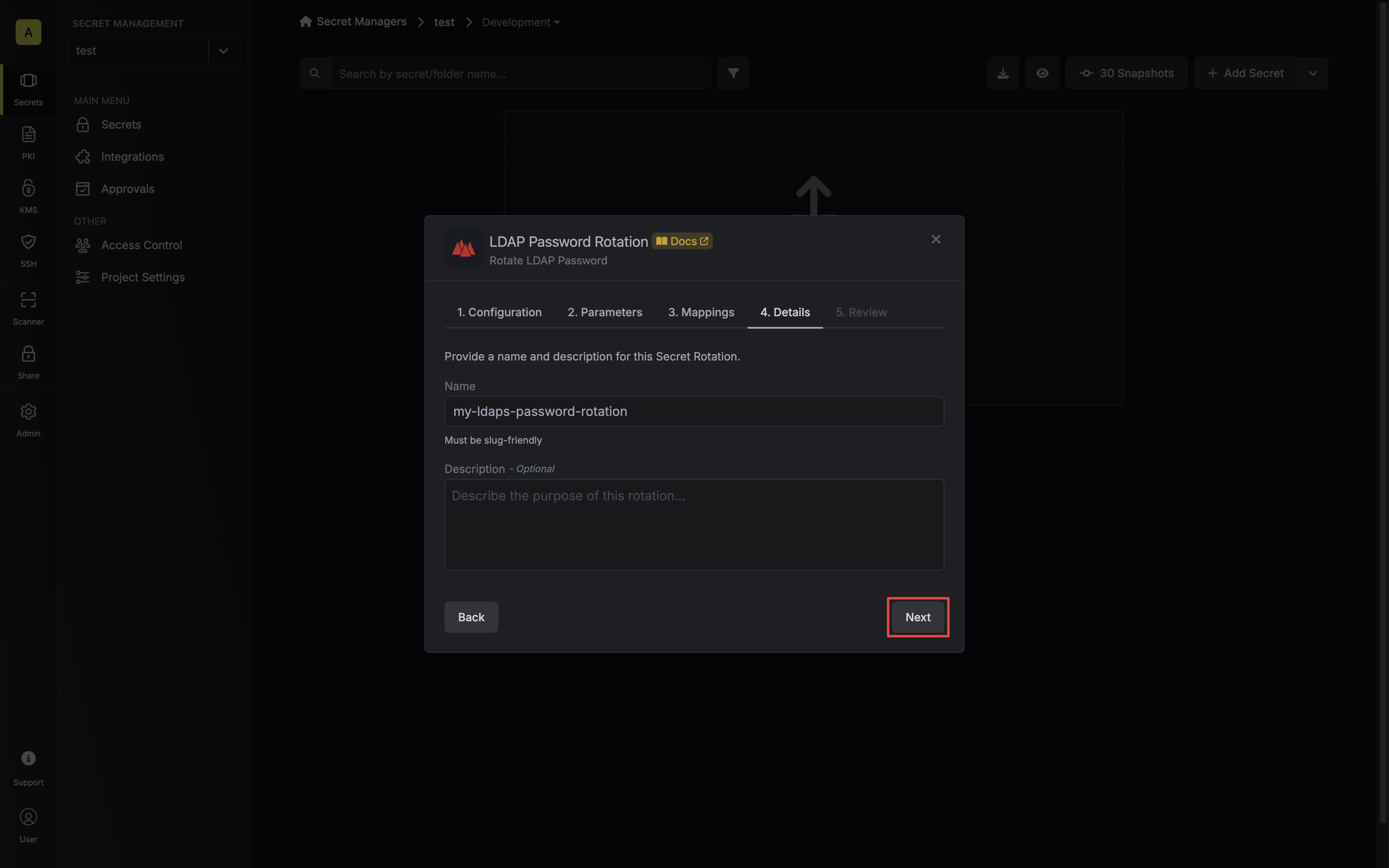
- Name - the name of the secret rotation configuration. Must be slug-friendly.
- Description (optional) - a description of this rotation configuration.
-
Review your configuration, then click Create Secret Rotation.
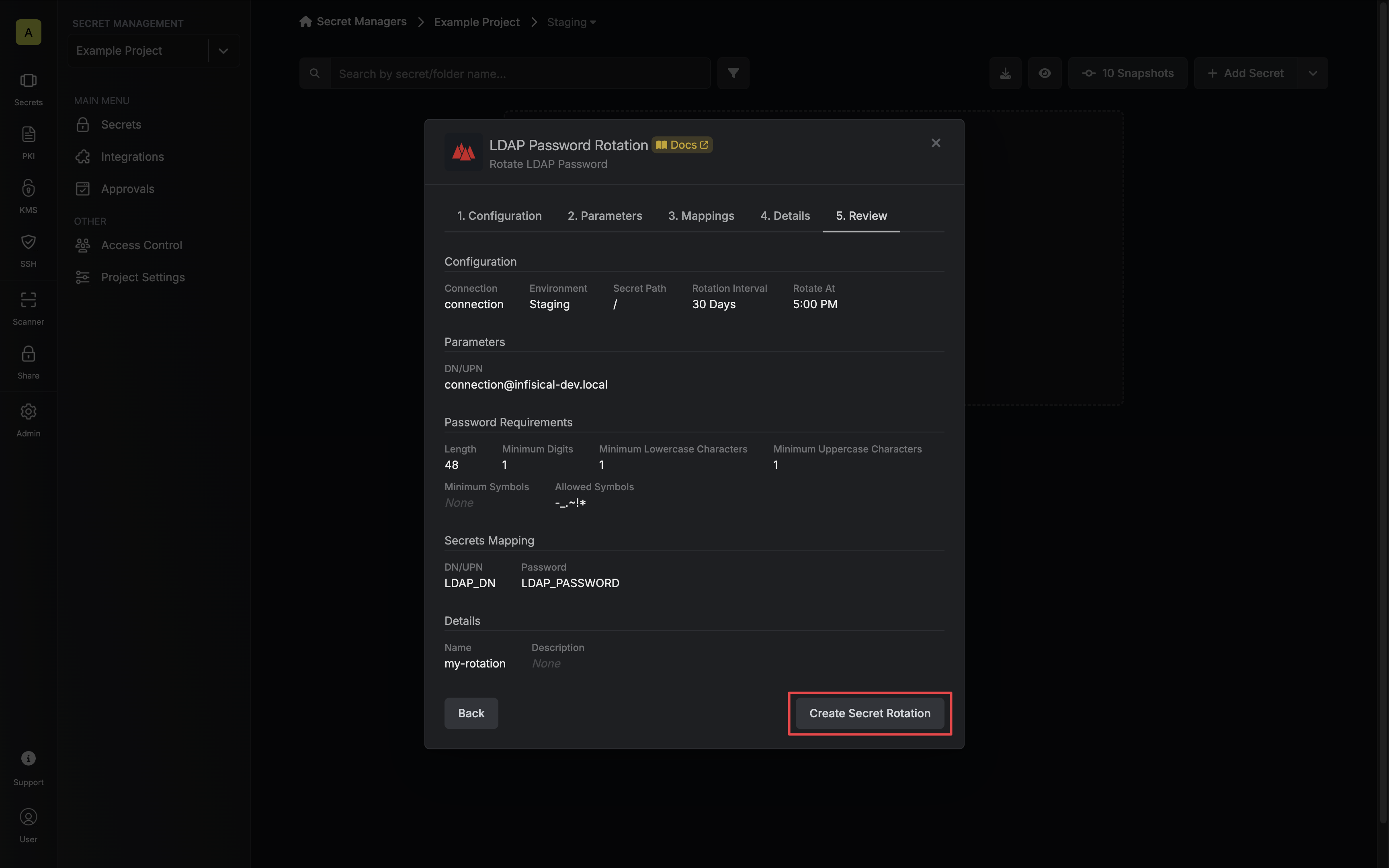
-
Your LDAP Password credentials are now available for use via the mapped secrets.