Concept
The Infisical ACME integration allows you to connect with ACME (Automatic Certificate Management Environment) Certificate Authorities to automatically issue and manage publicly trusted TLS certificates for your subscribers. This integration enables you to leverage established public CA infrastructure like Let’s Encrypt while centralizing your certificate management within Infisical. ACME is a protocol that automates the process of certificate issuance and renewal through domain validation challenges. The integration is perfect for obtaining trusted X.509 certificates for public-facing services and is capable of automatically renewing certificates as needed. As part of the workflow, you configure DNS provider credentials, register an ACME CA provider with Infisical, and create subscribers to represent the certificates you wish to issue. Each issued certificate is automatically managed through its lifecycle, including renewal before expiration. We recommend reading about ACME protocol and DNS-01 challenges for a fuller understanding of the underlying technology.Workflow
A typical workflow for using Infisical with ACME Certificate Authorities consists of the following steps:- Setting up AWS Route53 or Cloudflare credentials with appropriate DNS permissions.
- Creating an AWS/Cloudflare connection in Infisical to store the credentials.
- Registering an ACME Certificate Authority (like Let’s Encrypt) with Infisical.
- Creating subscribers that use the ACME CA as their issuing authority.
- Managing certificate lifecycle events such as issuance, renewal, and revocation through Infisical.
Understanding ACME DNS-01 Challenge
The DNS-01 challenge is the method used by ACME CA providers to verify that you control a domain before issuing a certificate. Here’s how Infisical handles this process:- Challenge Request: When you request a certificate, the ACME provider (like Let’s Encrypt) issues a challenge token.
-
DNS Record Creation: Infisical creates a TXT record at
_acme-challenge.<YOUR_DOMAIN>with a value derived from the challenge token. - DNS Propagation: The TXT record must propagate through the DNS system (usually takes a few minutes, depending on TTL settings).
- Validation: The ACME provider checks for the existence of this TXT record to verify domain control.
- Cleanup: After validation completes successfully, Infisical automatically removes the TXT record from your DNS.
Guide
In the following steps, we explore how to set up ACME Certificate Authority integration with Infisical using Let’s Encrypt as an example.1
Create App Connection with Required Permissions
Before proceeding with the ACME CA registration, you need to set up an App Connection with the appropriate permissions for DNS validation:Replace
- Route53
- Cloudflare
- Navigate to your Organization Settings > App Connections and create a new AWS connection.
- Ensure your AWS connection has the following minimum permissions for Route53 DNS validation:
YOUR_HOSTED_ZONE_ID with your actual Route53 hosted zone ID.For detailed instructions on setting up an AWS connection, see the AWS Connection documentation.2
Register ACME Certificate Authority
- Infisical UI
- API
1
Create ACME CA
To register an ACME CA, head to your Project > Internal PKI > Certificate Authorities and press the + button in the External Certificate Authorities section. Fill out the details for the ACME CA registration:
Fill out the details for the ACME CA registration: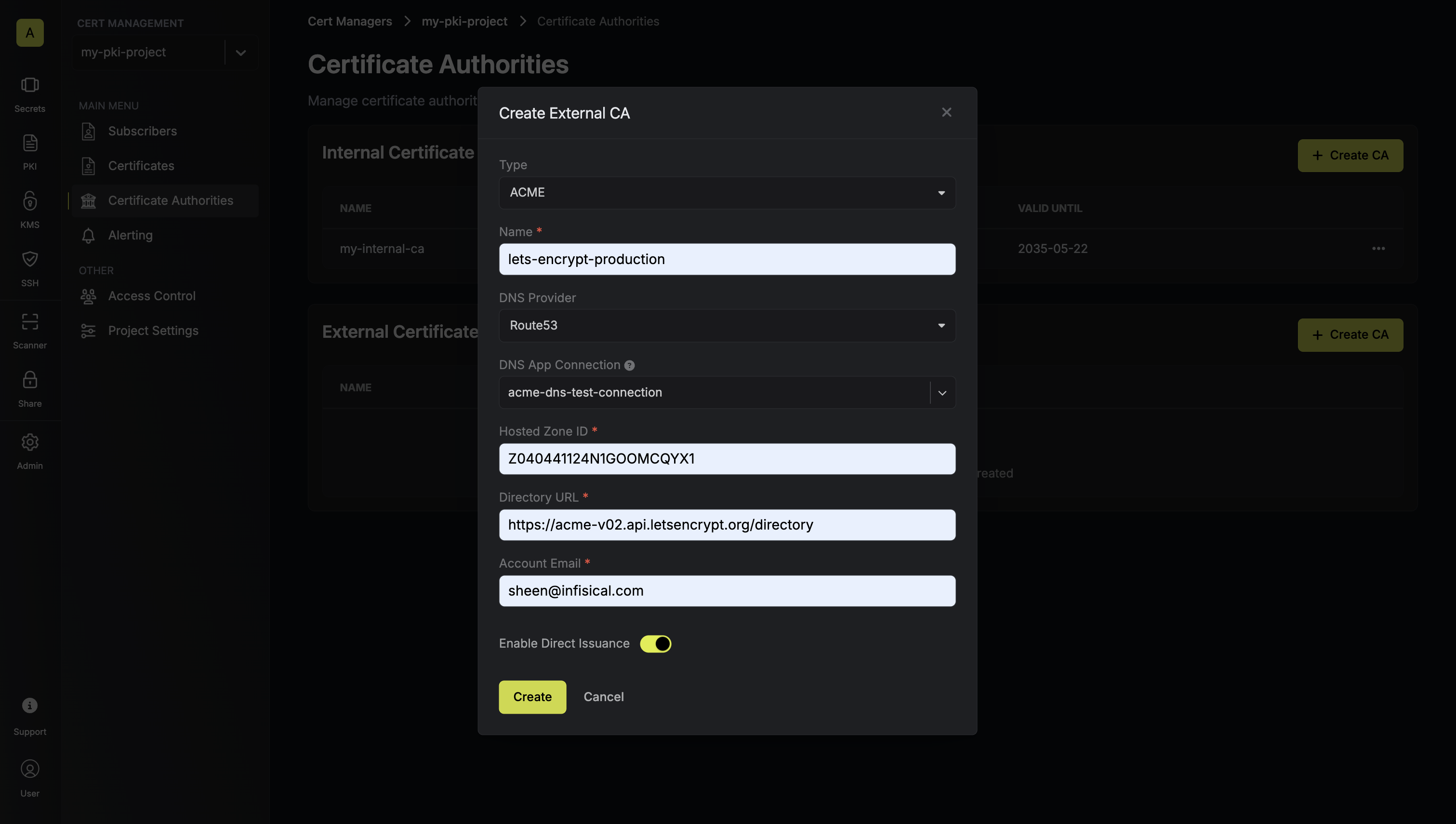 Here’s guidance on each field:
Here’s guidance on each field:
 Fill out the details for the ACME CA registration:
Fill out the details for the ACME CA registration: Here’s guidance on each field:
Here’s guidance on each field:- Type: Select “ACME” as the External CA type.
- Name: Enter a name for the ACME CA (e.g., “lets-encrypt-production”).
- DNS App Connection: Select from available DNS app connections or configure a new one. This connection provides Infisical with the credentials needed to create and remove DNS records for ACME validation.
- Zone ID: Enter the Zone ID for the domain(s) you’ll be requesting certificates for.
- Directory URL: Enter the ACME v2 directory URL for your chosen CA provider (e.g.,
https://acme-v02.api.letsencrypt.org/directoryfor Let’s Encrypt). - Account Email: Email address to associate with your ACME account. This email will receive important notifications about your certificates.
- Enable Direct Issuance: Toggle on to allow direct certificate issuance without requiring subscribers.
- EAB Key Identifier (KID): (Optional) The Key Identifier (KID) provided by your ACME CA for External Account Binding (EAB). This is required by some ACME providers (e.g., ZeroSSL, DigiCert) to link your ACME account to an external account you’ve pre-registered with them.
- EAB HMAC Key: (Optional) The HMAC Key provided by your ACME CA for External Account Binding (EAB). This key is used in conjunction with the KID to prove ownership of the external account during ACME account registration.
2
Verify ACME CA Registration
Once registered, your ACME CA will appear in the External Certificate Authorities section. From here, you can:
From here, you can:
 From here, you can:
From here, you can:- View the status of the ACME CA registration
- Edit the configuration settings
- Disable or re-enable the ACME CA
- Delete the ACME CA registration if no longer needed
3
Create Subscriber for ACME CA
Next, create a subscriber that uses your ACME CA for certificate issuance. Navigate to your Project > Subscribers and create a new subscriber.Configure the subscriber with:
- Issuing CA: Select your registered ACME CA
- Common Name: The domain for which you want to issue certificates (e.g.,
example.com) - Alternative Names: Additional domains to include in the certificate
4
Issue Certificate
Once your subscriber is configured, you can issue certificates either through the Infisical UI or programmatically via the API.When you request a certificate:
- Infisical generates a key pair for the certificate
- Sends a Certificate Signing Request (CSR) to the ACME CA
- Receives a DNS-01 challenge from the ACME provider
- Creates a TXT record in Route53/Cloudflare to satisfy the challenge
- Notifies the ACME provider that the challenge is ready for validation
- Once validated, the ACME provider issues the certificate
- Infisical stores and manages the certificate for your subscriber
5
Use Certificate in Your Applications
The issued certificate and private key are now available through Infisical and can be:
- Downloaded directly from the Infisical UI
- Retrieved via the Infisical API for programmatic access using the latest certificate bundle endpoint
Example: Let’s Encrypt Integration
Let’s Encrypt is a free, automated, and open Certificate Authority that provides domain-validated SSL/TLS certificates. Here’s how the integration works with Infisical:Production Environment
- Directory URL:
https://acme-v02.api.letsencrypt.org/directory - Rate Limits: 50 certificates per registered domain per week
- Certificate Validity: 90 days with automatic renewal
- Trusted By: All major browsers and operating systems
Staging Environment (for testing)
- Directory URL:
https://acme-staging-v02.api.letsencrypt.org/directory - Rate Limits: Much higher limits for testing
- Certificate Validity: 90 days (not trusted by browsers)
- Use Case: Testing your ACME integration without hitting production rate limits
Always test your ACME integration using Let’s Encrypt’s staging environment first. This allows you to verify your DNS configuration and certificate issuance process without consuming your production rate limits.
Example: DigiCert Integration
DigiCert is a leading commercial Certificate Authority providing a wide range of trusted SSL/TLS certificates. Infisical can integrate with DigiCert’s ACME service to automate the provisioning and management of these certificates.- Directory URL:
https://acme.digicert.com/v2/acme/directory - External Account Binding (EAB): Required. You will need a Key Identifier (KID) and HMAC Key from your DigiCert account to register the ACME CA in Infisical.
- Certificate Validity: Typically 90 days, with automatic renewal through Infisical.
- Trusted By: All major browsers and operating systems.
When integrating with DigiCert ACME, ensure you have obtained the necessary External Account Binding (EAB) Key Identifier (KID) and HMAC Key from your DigiCert account.
FAQ
What DNS validation methods are supported?
What DNS validation methods are supported?
Currently, Infisical supports DNS-01 validation through AWS Route53 or Cloudflare. The DNS-01 challenge method is preferred for ACME integrations because it:
- Works with wildcard certificates
- Doesn’t require your servers to be publicly accessible
- Can be fully automated without manual intervention
Can I use wildcard certificates with ACME CAs?
Can I use wildcard certificates with ACME CAs?
Yes! ACME CAs like Let’s Encrypt support wildcard certificates (e.g.,
*.example.com) when using DNS-01 validation. Simply specify the wildcard domain in your subscriber configuration.Note that wildcard certificates still require DNS-01 validation - HTTP-01 validation cannot be used for wildcard certificates.How long are ACME certificates valid?
How long are ACME certificates valid?
Most ACME providers issue certificates with 90-day validity periods. This shorter validity period is designed to:
- Encourage automation of certificate management
- Reduce the impact of compromised certificates
- Ensure systems stay up-to-date with certificate management practices
Can I use multiple ACME providers?
Can I use multiple ACME providers?
Yes! You can register multiple ACME CAs in the same project:
- Different providers for different domains or use cases
- Staging and production environments for the same provider
- Backup providers for redundancy

