Concept
In Infisical PKI, subscribers are logical representations of entities such as devices, servers, applications that request and receive certificates from Certificate Authorities (CAs).Workflow
The typical workflow for managing subscribers consists of the following steps:- Creating a subscriber and defining which (issuing) CA will issue X.509 certificates for it as well as attributes to be included on the certificates including common name, subject alternative names, TTL, etc. You can also optionally configure automatic certificate renewal.
- Requesting for a certificate against the subscriber with or without a certificate signing request (CSR).
- Managing certificate lifecycle events such as certificate renewal and revocation. As part of the certificate revocation flow, you can also query for a Certificate Revocation List CRL, a time-stamped, signed data structure issued by a CA containing a list of revoked certificates to check if a certificate has been revoked.
Note that this workflow can be executed via the Infisical UI or manually such
as via API.
Guide to Issuing Certificates with Subscribers
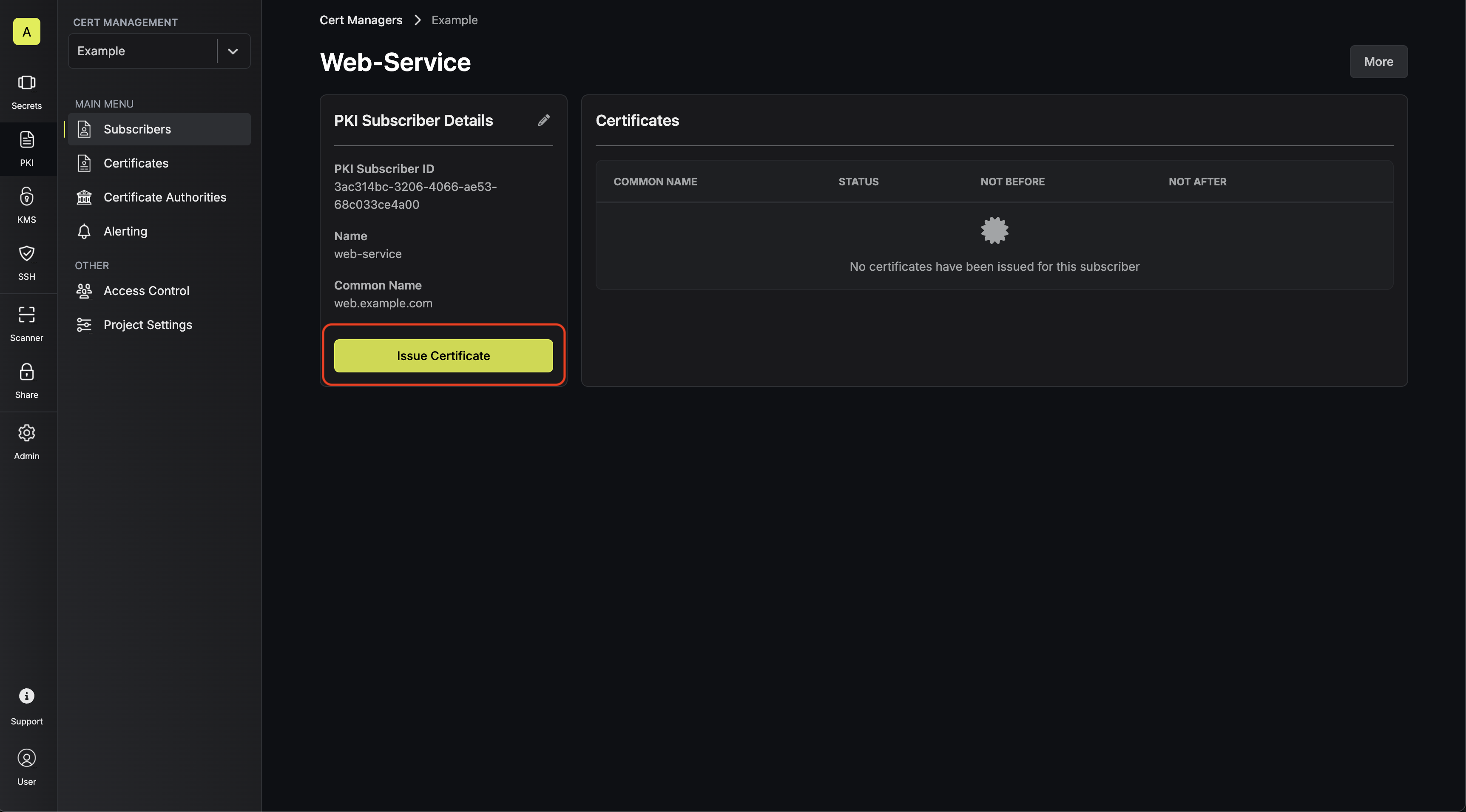
In the following steps, we explore how to issue a X.509 certificate for a subscriber.Creating a subscriber
A subscriber is the logical representation of an entity that requests and
receives certificates from a CA. With a subscriber, you can specify the
attributes that must be present on the X.509 certificates issued for it.Head to your Infisical PKI Project > Subscribers to create a subscriber. The PKI Subscriber modal is organized into two tabs:
The PKI Subscriber modal is organized into two tabs: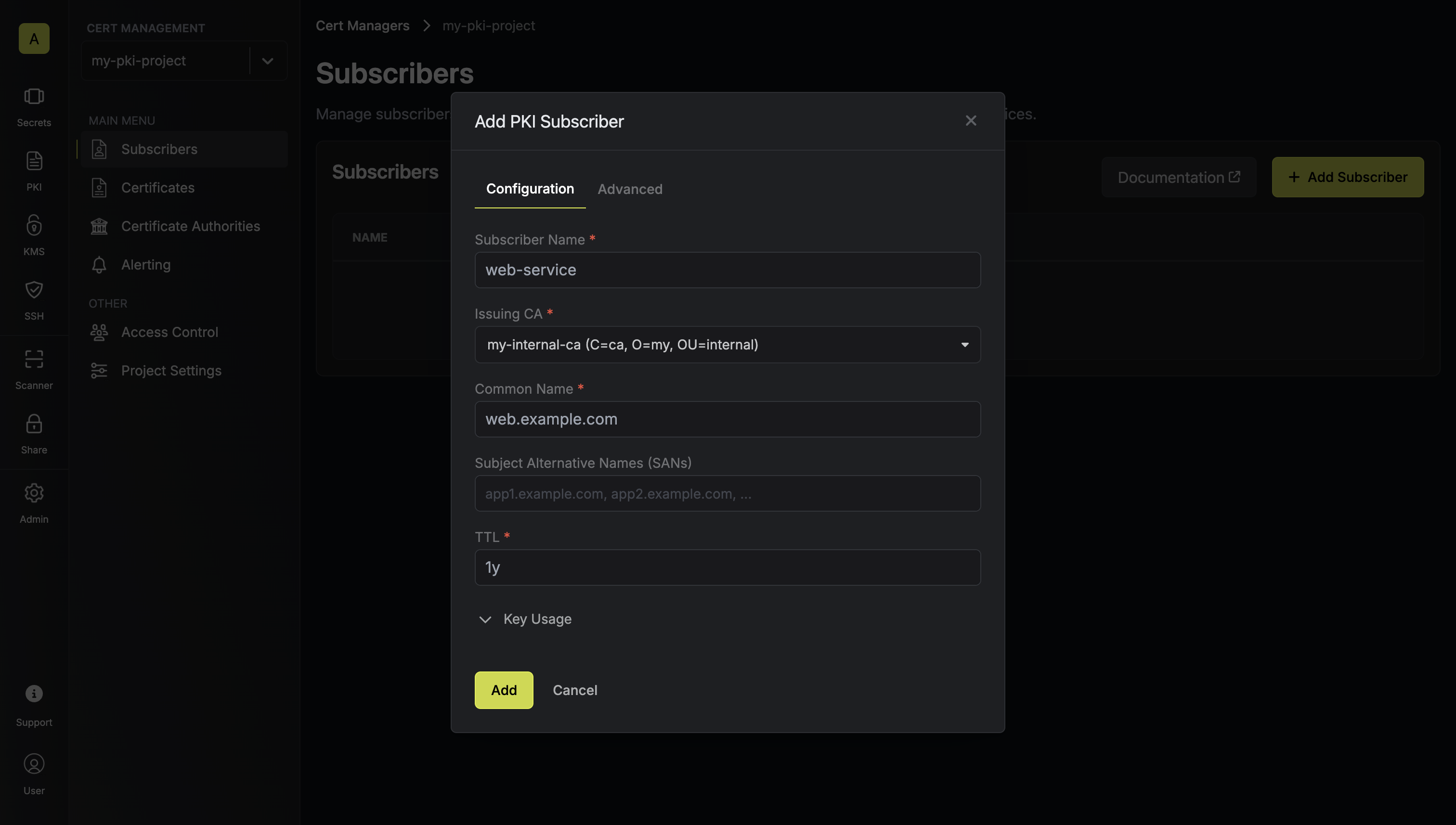 This tab contains the core certificate attributes and settings:
This tab contains the core certificate attributes and settings: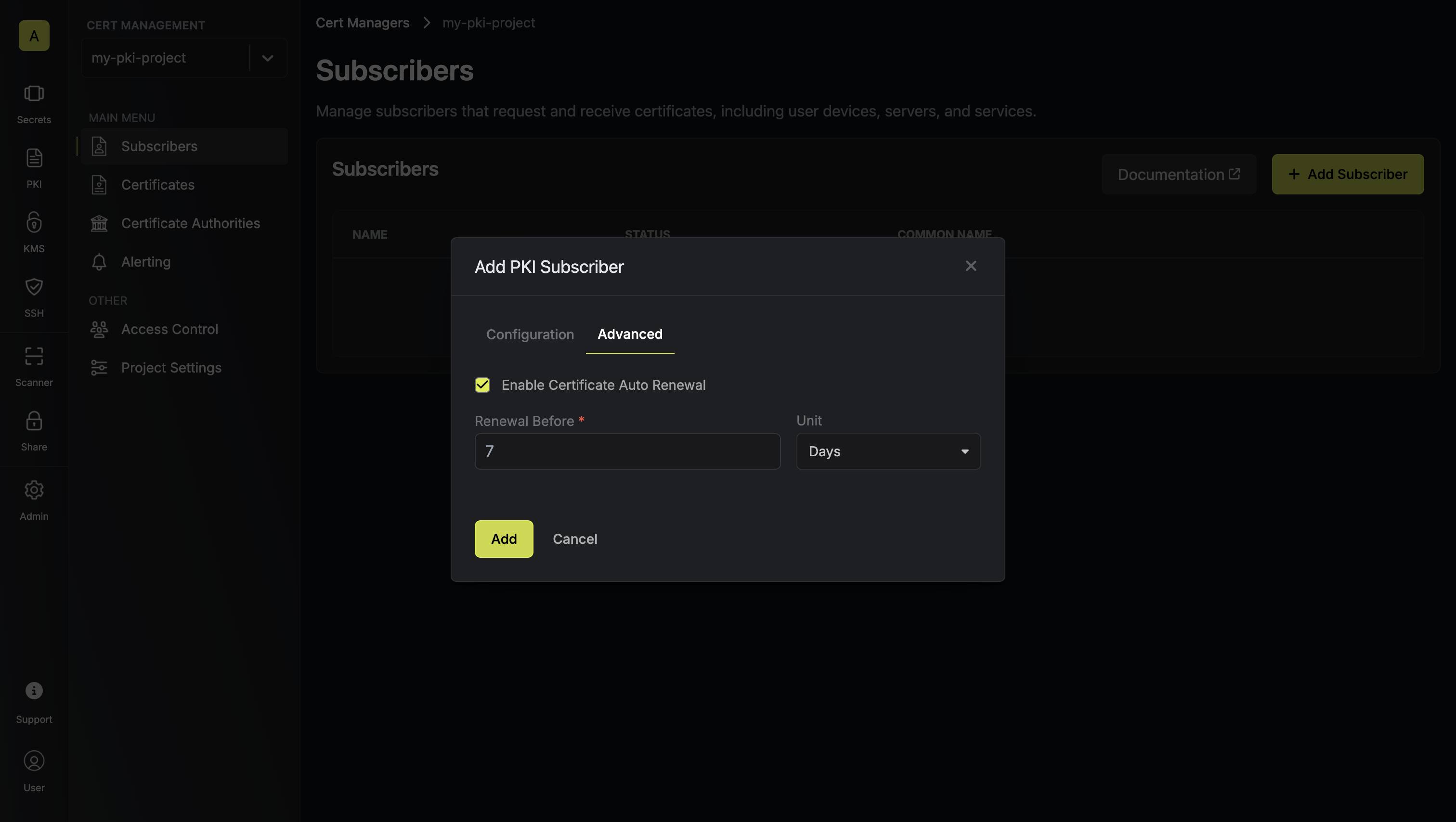 This tab contains optional advanced features:
This tab contains optional advanced features:
 The PKI Subscriber modal is organized into two tabs:
The PKI Subscriber modal is organized into two tabs:Configuration Tab
 This tab contains the core certificate attributes and settings:
This tab contains the core certificate attributes and settings:- Subscriber Name: A slug-friendly name for the subscriber such as
web-service. - Issuing CA: The Certificate Authority (CA) that will issue X.509 certificates for the subscriber.
- Common Name (CN): The common name to be included on certificates to be issued to the subscriber.
- Subject Alternative Names (SANs): A comma-delimited list of Subject Alternative Names (SANs) to be included on certificates; these can be hostnames or email addresses like
app1.acme.com, app2.acme.com. - TTL: The lifetime of the certificate.
- Key Usage: The key usage extension of the certificate.
- Extended Key Usage: The extended key usage extension of the certificate.
Advanced Tab
 This tab contains optional advanced features:
This tab contains optional advanced features:- Certificate Auto Renewal: Toggle to enable automatic certificate renewal for this subscriber.
- Renewal Before Expiry: When auto renewal is enabled, specify how many days before certificate expiry the system should automatically issue a new certificate (e.g., 7 days).
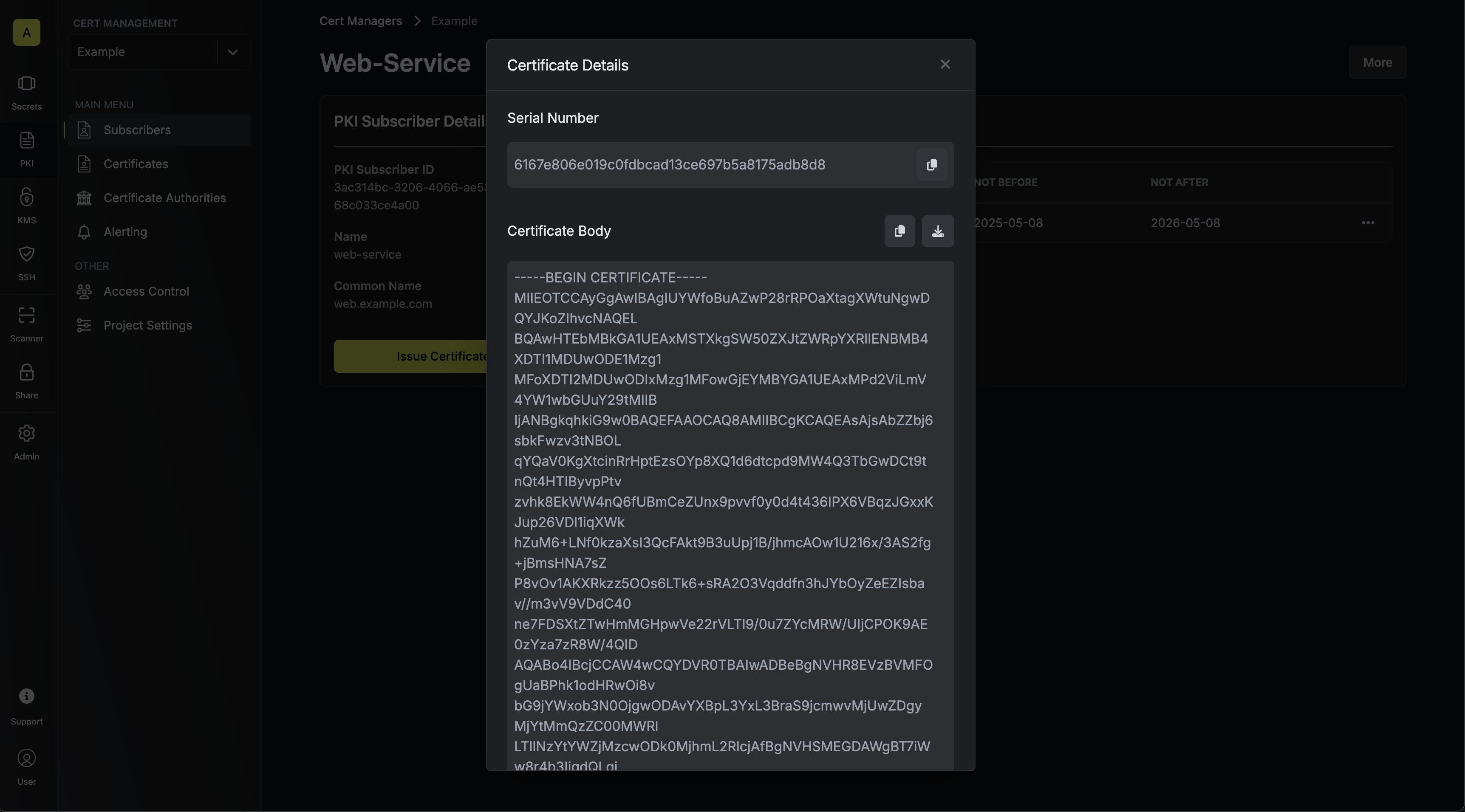
It’s possible to issue certificates for a subscriber with or without a certificate signing request (CSR).
- If requesting without a CSR, the attributes specified on the subscriber will be used to issue a certificate for the subscriber.
- If requesting with a CSR, the attributes on it will be validated against the attributes specified on the subscriber and a certificate is only issued if they comply.
When Certificate Auto Renewal is enabled, the system will automatically issue new certificates before the current ones expire, ensuring continuous certificate availability without manual intervention.
Guide to Revoking Certificates
In the following steps, we explore how to revoke a X.509 certificate and obtain a Certificate Revocation List (CRL) for a CA.Revoking a Certificate
Assuming that you’ve issued a certificate for a subscriber, you can revoke it by
selecting the Revoke Certificate option on the certificate you wish to revoke
on the subscriber’s page.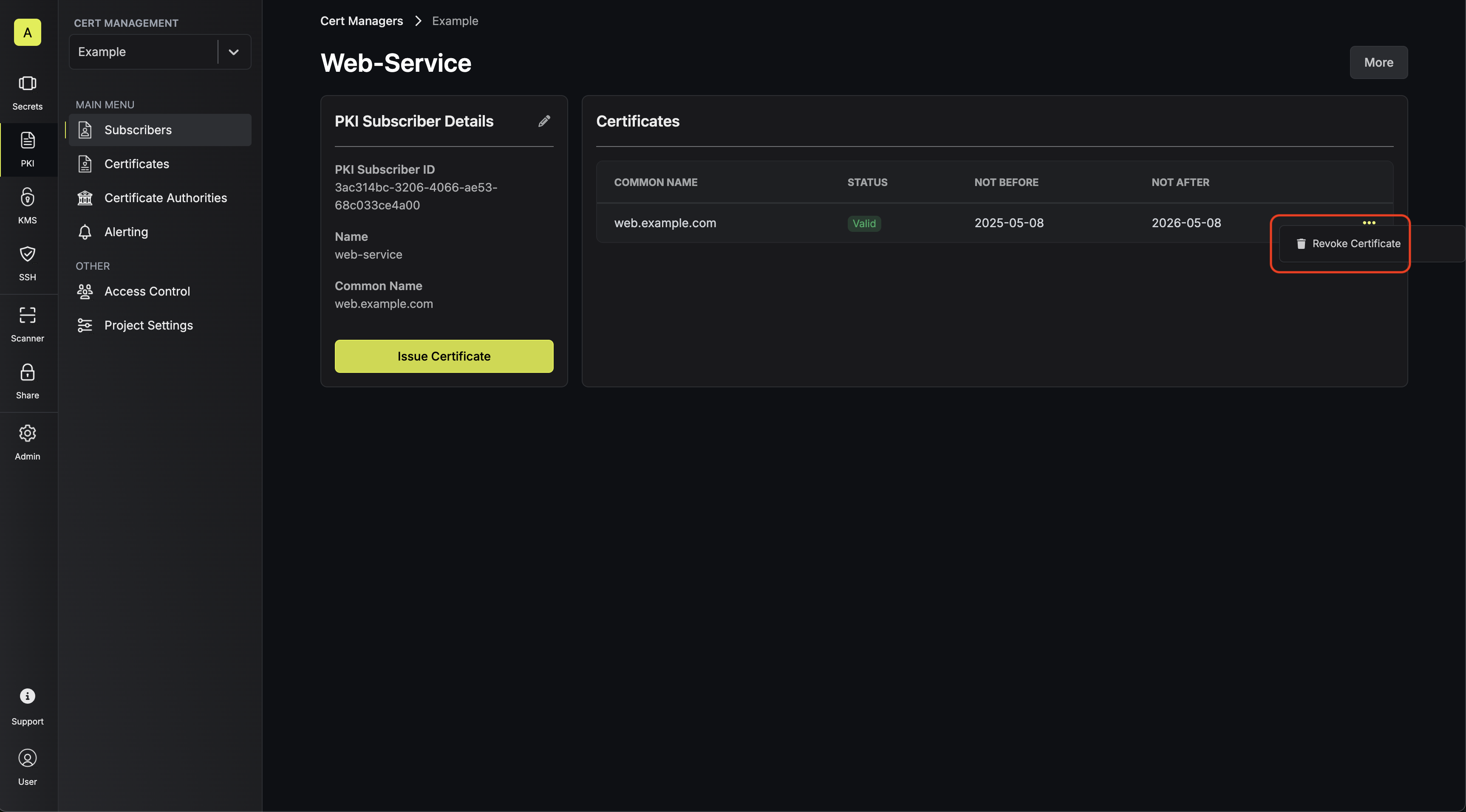

Obtaining a CRL
In order to check the revocation status of a certificate, you can check it
against the CRL of a CA by heading to its Issuing CA and downloading the CRL.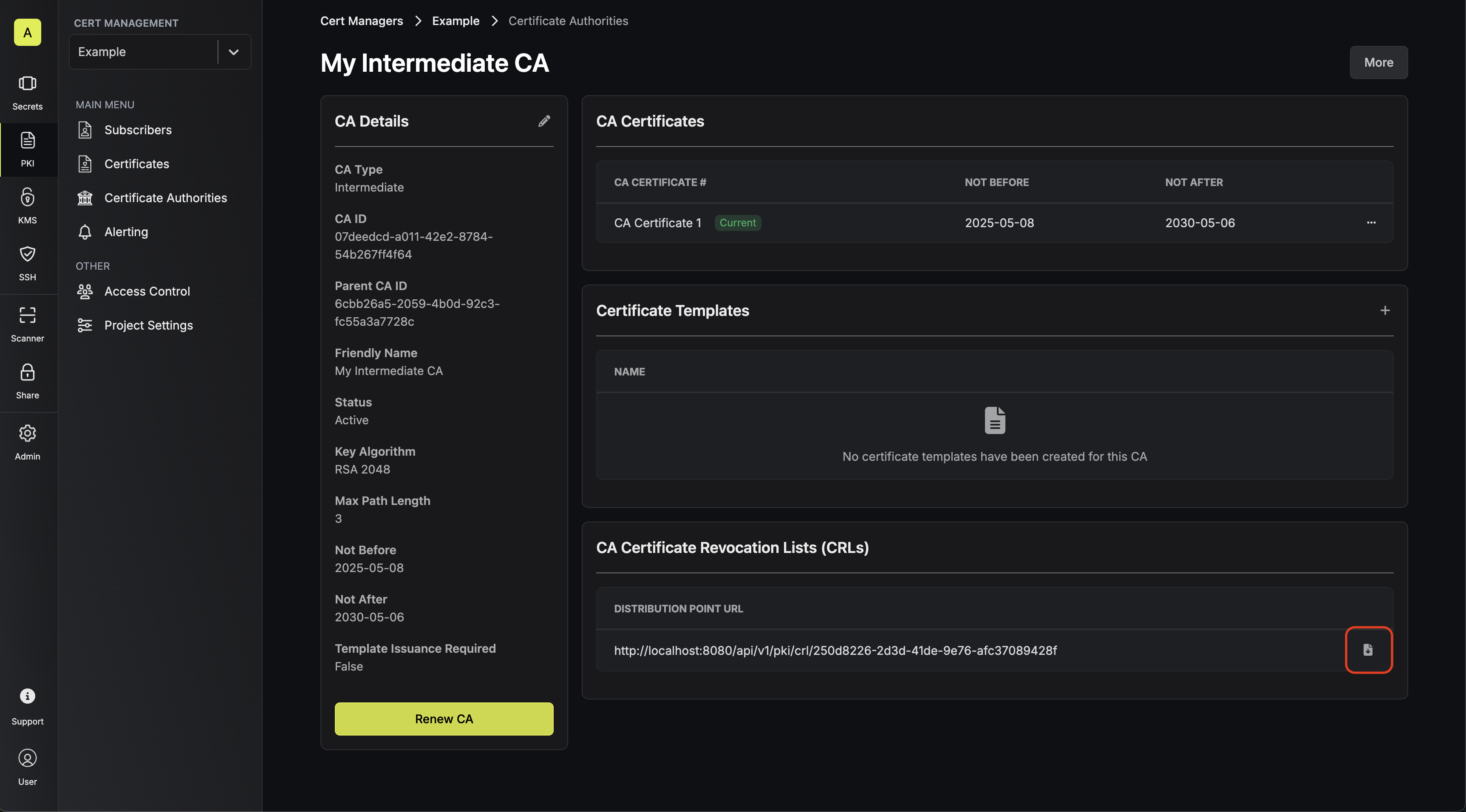 To verify a certificate against the
downloaded CRL with OpenSSL, you can use the following command:Note that you can also obtain the CRL from the certificate itself by
referencing the CRL distribution point extension on the certificate.To check a certificate against the CRL distribution point specified within it with OpenSSL, you can use the following command:
To verify a certificate against the
downloaded CRL with OpenSSL, you can use the following command:Note that you can also obtain the CRL from the certificate itself by
referencing the CRL distribution point extension on the certificate.To check a certificate against the CRL distribution point specified within it with OpenSSL, you can use the following command:
 To verify a certificate against the
downloaded CRL with OpenSSL, you can use the following command:
To verify a certificate against the
downloaded CRL with OpenSSL, you can use the following command:FAQ
What is the workflow for renewing a certificate?
What is the workflow for renewing a certificate?
To renew a certificate, you have two options:Manual Renewal: Issue a new certificate for the same subscriber. The original certificate will continue to be valid through its original TTL unless explicitly revoked.Automatic Renewal: If Certificate Auto Renewal is enabled for the subscriber, the system will automatically issue new certificates before the current ones expire based on the configured renewal period.
How does Certificate Auto Renewal work?
How does Certificate Auto Renewal work?
When Certificate Auto Renewal is enabled for a subscriber, the system monitors certificate expiration dates and automatically issues new certificates before they expire. You can configure how many days before expiry the renewal should occur (e.g., 7 days before expiration). This ensures continuous certificate availability without manual intervention.