Prerequisites
Before setting up ADCS integration, ensure you have:- Microsoft Active Directory Certificate Services (ADCS) server running and accessible
- Domain administrator account with certificate management permissions
- ADCS web enrollment enabled on your server
- Network connectivity from Infisical to the ADCS server
- IP whitelisting: Your ADCS server must allow connections from Infisical’s IP addresses
- For Infisical Cloud instances, see Networking Configuration for the list of IPs to whitelist
- For self-hosted instances, whitelist your Infisical server’s IP address
- Azure ADCS app connection configured (see Azure ADCS Connection)
Complete Workflow: From Setup to Certificate Issuance
This section walks you through the complete end-to-end process of setting up Azure ADCS integration and issuing your first certificate.1
Navigate to External Certificate Authorities
In your Infisical project, go to your Certificate Project → Certificate Authority to access the external CAs page.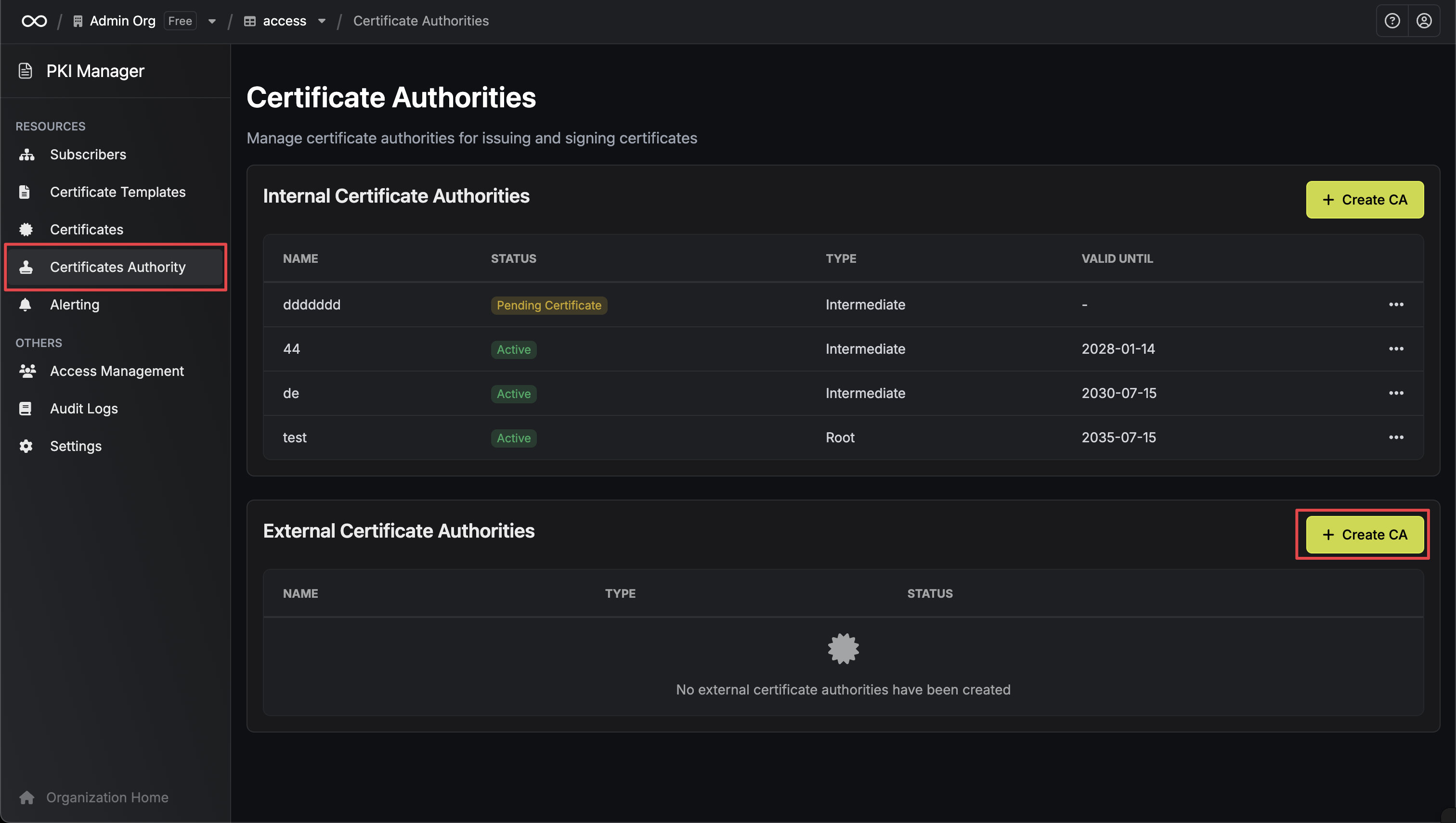

2
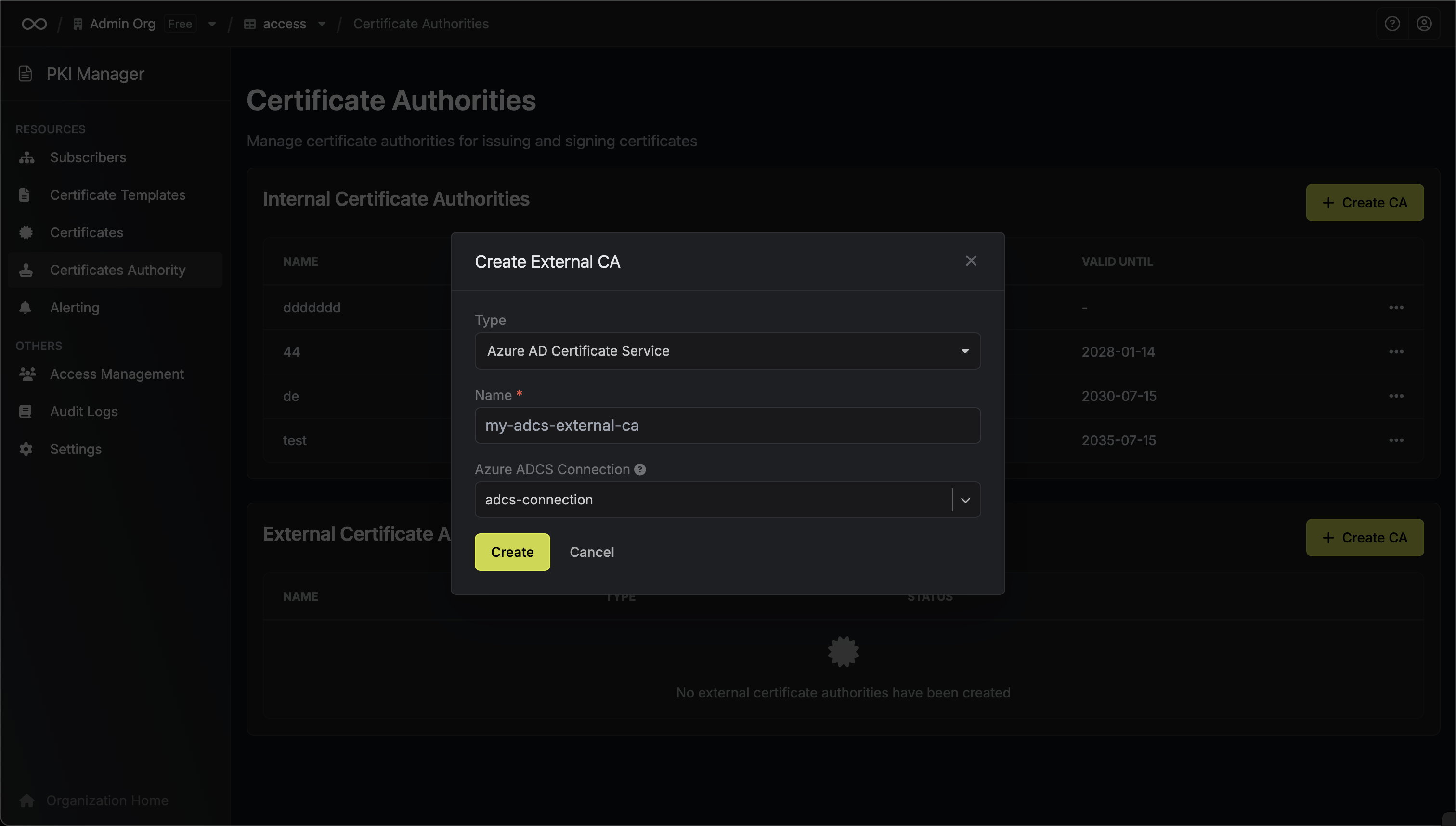
Create New Azure ADCS Certificate Service CA
Click Create CA and configure:
- Type: Choose Azure AD Certificate Service
- Name: Friendly name for this CA (e.g., “Production ADCS CA”)
-
App Connection: Choose your ADCS connection from the dropdown
3
Certificate Authority Created
Once created, your Azure ADCS Certificate Authority will appear in the list and be ready for use.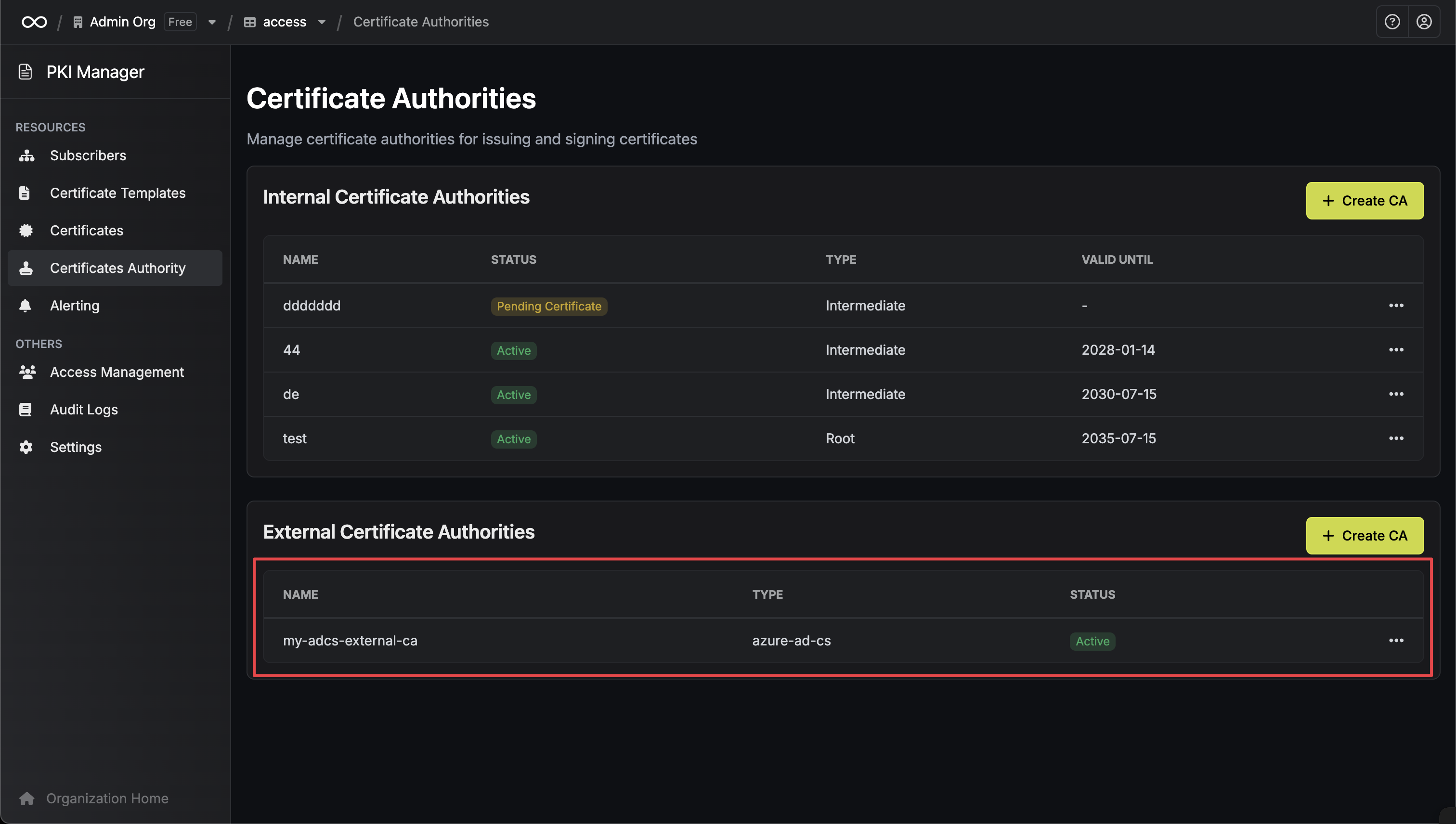

4
Navigate to Subscribers
Go to Subscribers to access the subscribers page.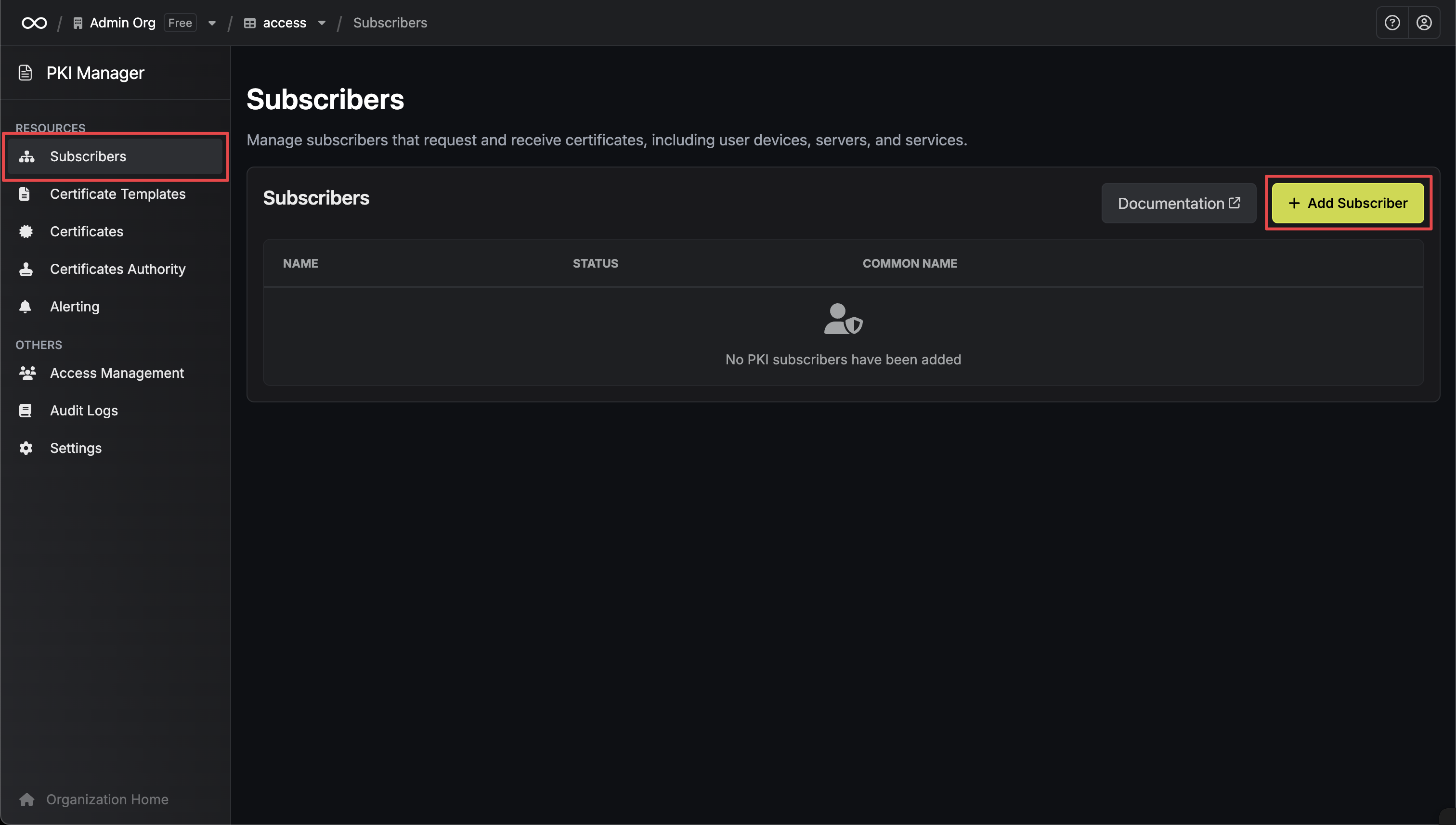

5
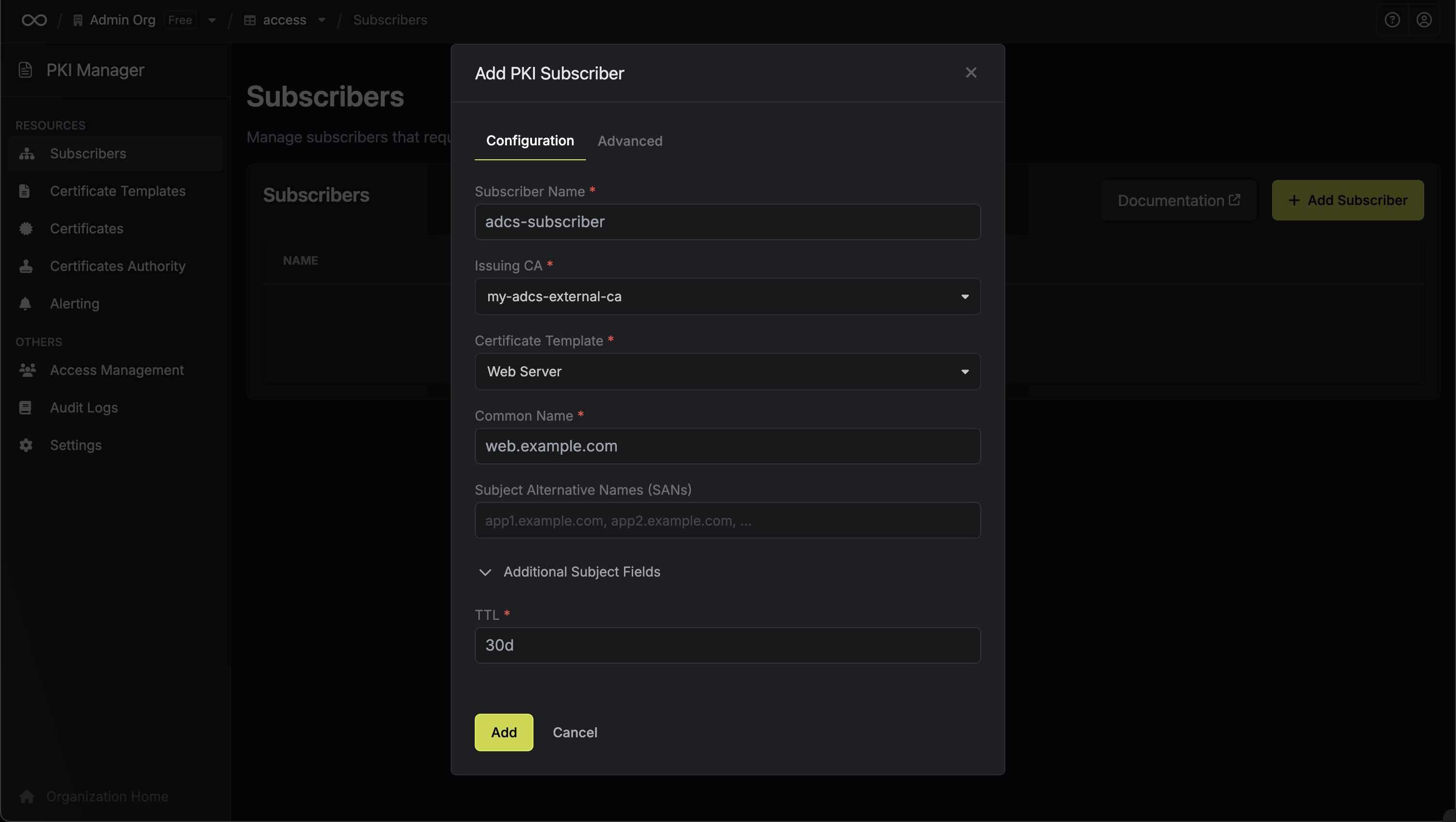
Create New Subscriber
Click Add Subscriber and configure:
- Name: Unique subscriber name (e.g., “web-server-certs”)
- Certificate Authority: Select your ADCS CA
- Common Name: Certificate CN (e.g., “api.example.com”)
- Certificate Template: Select from dynamically loaded ADCS templates
- Subject Alternative Names: DNS names, IP addresses, or email addresses
- TTL: Certificate validity period (e.g., “1y” for 1 year)
-
Additional Subject Fields: Organization, OU, locality, state, country, email (if required by template)
6
Subscriber Created
Your subscriber is now created and ready to issue certificates.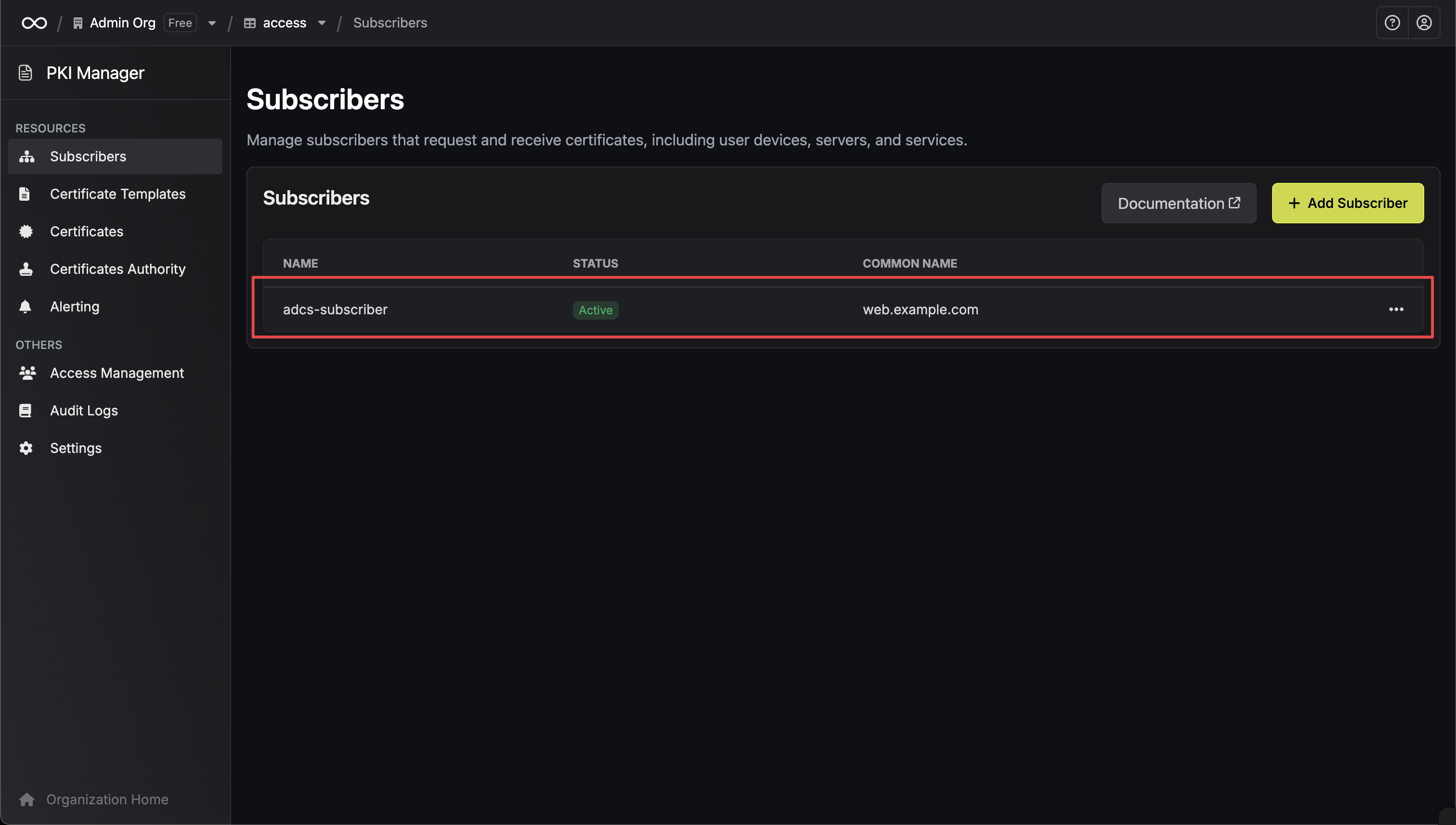

7
Issue New Certificate
Click into your subscriber and click Order Certificate to generate a new certificate using your ADCS template.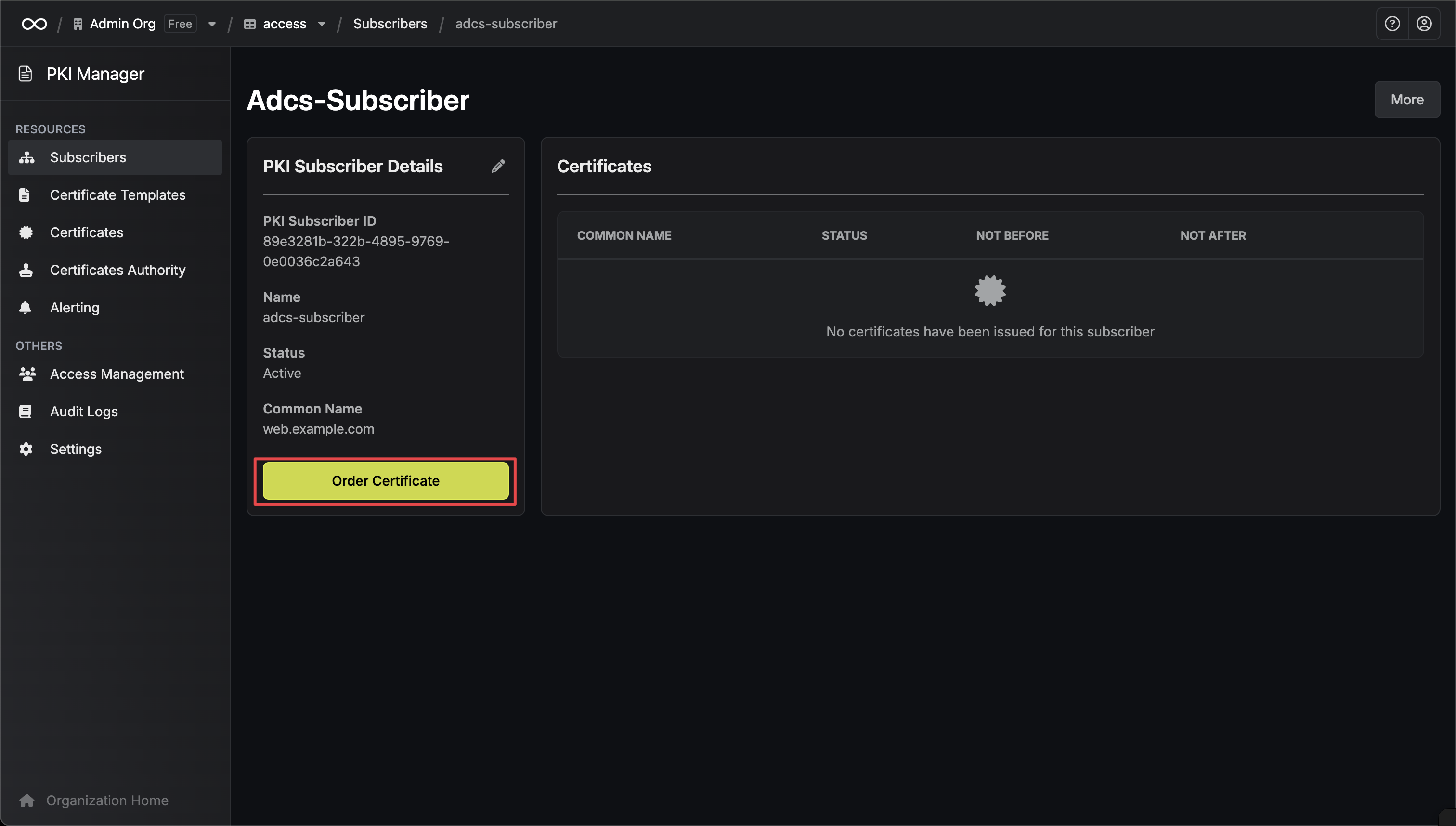

8
Certificate Created
Your certificate has been successfully issued by the ADCS server and is ready for use.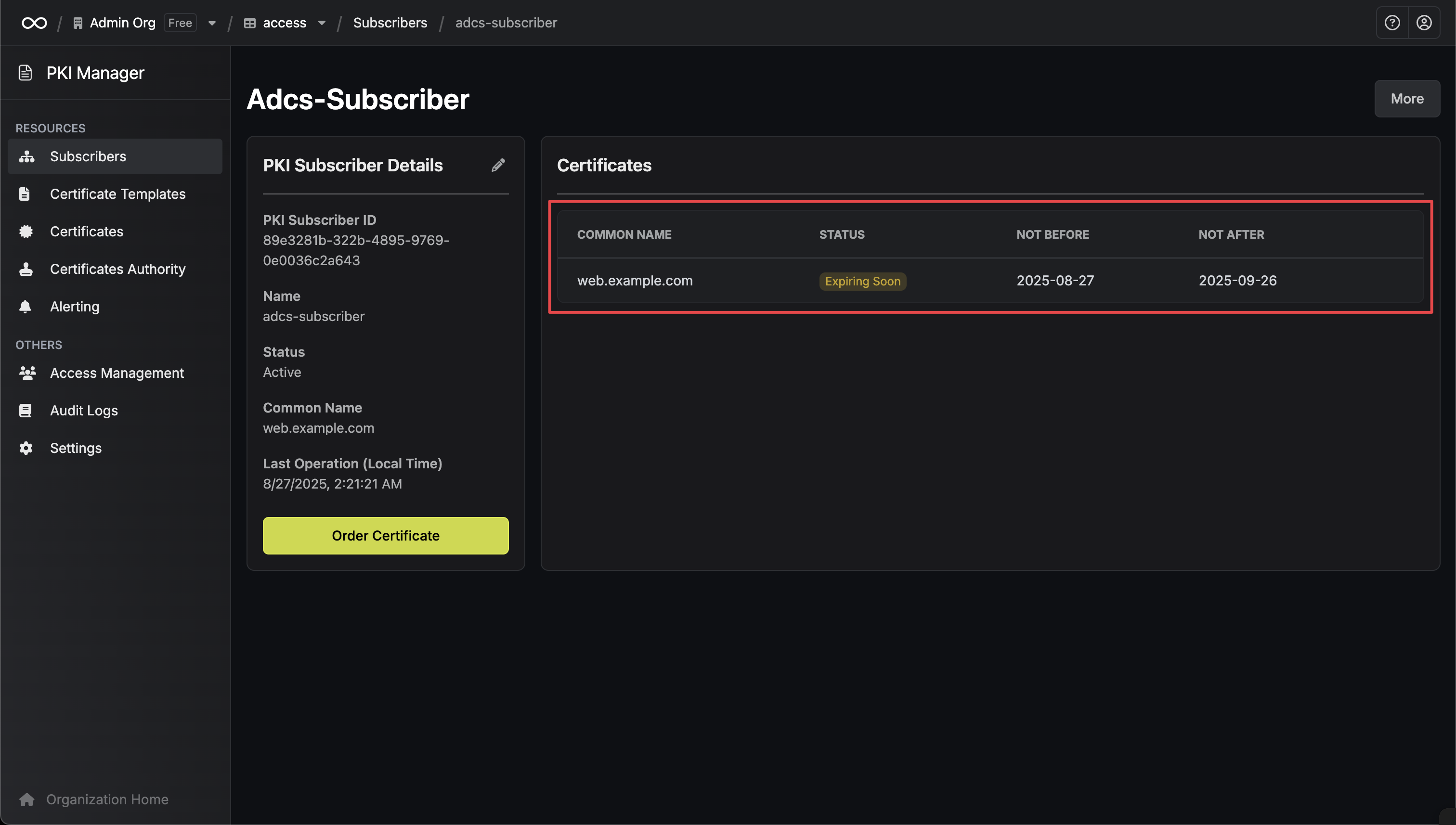

9
View Certificate Details
Navigate to Certificates to view detailed information about all issued certificates, including expiration dates, serial numbers, and certificate chains.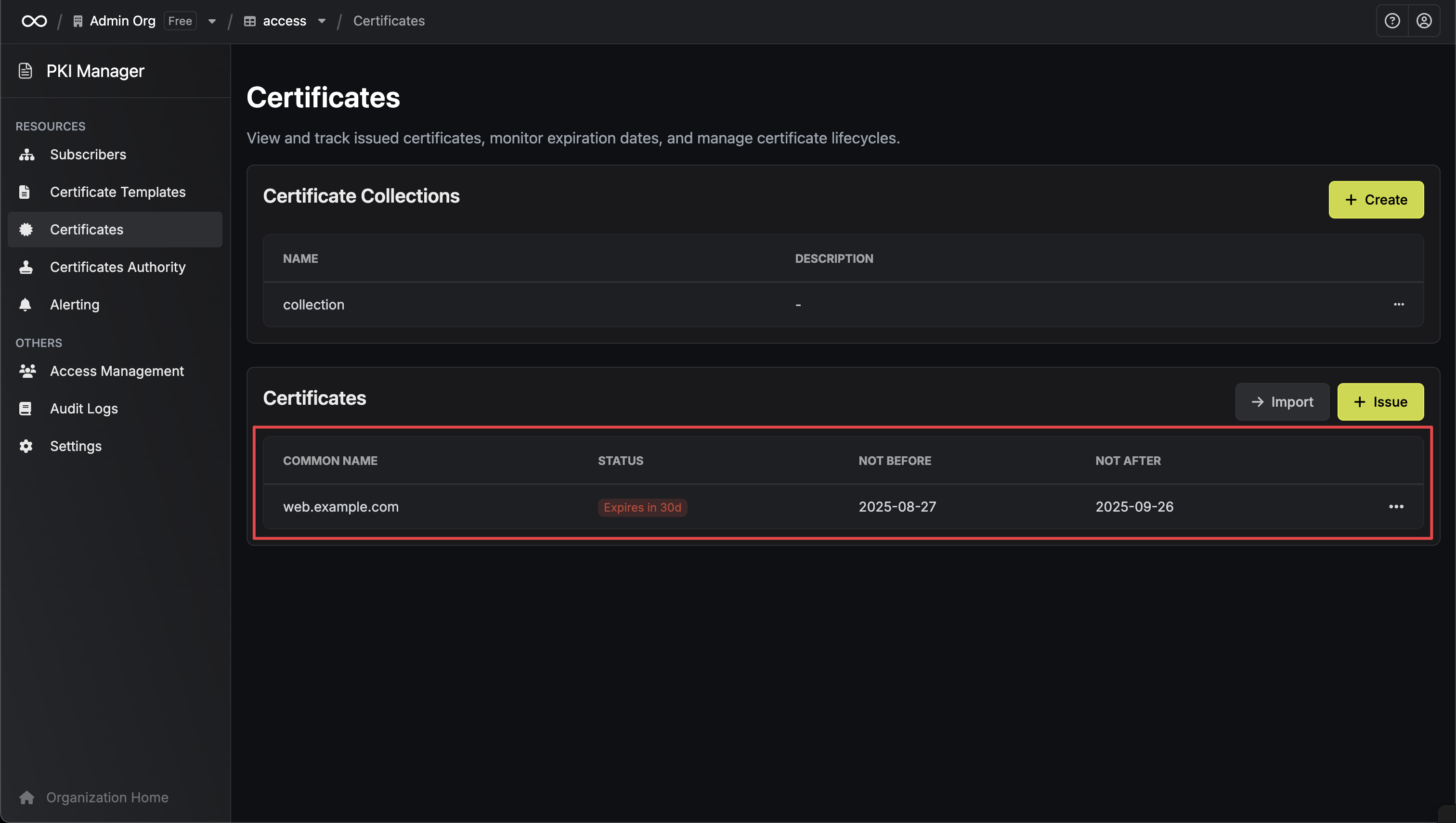

Certificate Templates
Infisical automatically retrieves available certificate templates from your ADCS server, ensuring you can only select templates that are properly configured and accessible. The system dynamically discovers templates during the certificate authority setup and certificate issuance process.Common Template Types
ADCS templates you might see include:- Web Server: For SSL/TLS certificates with server authentication
- Computer: For machine authentication certificates
- User: For client authentication certificates
- Basic EFS: For Encrypting File System certificates
- EFS Recovery Agent: For EFS data recovery
- Administrator: For administrative certificates
- Subordinate Certification Authority: For issuing CA certificates
Template Requirements
Ensure your ADCS templates are configured with:- Enroll permissions for your connection account
- Auto-enroll permissions if using automated workflows
- Subject name requirements matching your certificate requests
- Key usage extensions appropriate for your use case
Dynamic Template Discovery: Infisical queries your ADCS server in real-time to populate available templates. Only templates you have permission to use will be displayed during certificate issuance.
Certificate Issuance Limitations
Immediate Issuance Only
Manual Approval Not Supported: Infisical currently supports only immediate certificate issuance. Certificates that require manual approval or are held by ADCS policies cannot be issued through Infisical yet.
- Auto-approve certificate requests without manual intervention
- Not require administrator approval for the templates you plan to use
- Allow the connection account to request and receive certificates immediately
What Happens with Manual Approval
If a certificate request requires manual approval:- The request will be submitted to ADCS successfully
- Infisical will attempt to retrieve the certificate with exponential backoff (up to 5 retries over ~1 minute)
- If the certificate is not approved within this timeframe, the request will fail
- No background polling: Currently, Infisical does not check for certificates that might be approved hours or days later
Future Enhancement: Background polling for delayed certificate approvals is planned for future releases.
Certificate Revocation
Certificate revocation is not supported by the Azure ADCS connector due to security and complexity considerations.
Advanced Configuration
Custom Validity Periods
Enable custom certificate validity periods on your ADCS server:Troubleshooting
Common Issues
Certificate Request Denied- Verify ADCS template permissions for your connection account
- Check template subject name requirements
- Ensure template allows the requested key algorithm and size
- Verify IIS is running and the revocation endpoint is accessible
- Check IIS application pool permissions
- Test endpoint connectivity from Infisical
- Verify template exists on ADCS server and is published
- Check that your connection account has enrollment permissions for the template
- Ensure the template is properly configured and available in the ADCS web enrollment interface
- Templates are dynamically loaded - refresh the PKI Subscriber form if templates don’t appear
- Check if your ADCS template requires manual approval - Infisical only supports immediate issuance
- Verify the certificate template is configured for auto-approval
- Ensure your connection account has sufficient permissions to request certificates without approval
- Review ADCS server policies that might be holding the certificate request
- Verify your ADCS server’s firewall allows connections from Infisical
- For Infisical Cloud: Ensure Infisical’s IP addresses are whitelisted (see Networking Configuration)
- For self-hosted: Whitelist your Infisical server’s IP address on the ADCS server
- Test HTTPS connectivity to the ADCS web enrollment endpoint
- Check for any network security appliances blocking the connection
- Verify ADCS connection credentials
- Check domain account permissions
- Ensure network connectivity to ADCS server
- For ADCS servers with self-signed or private certificates: disable “Reject Unauthorized” in the SSL tab of your Azure ADCS app connection, or provide the certificate in PEM format
- Common SSL errors:
UNABLE_TO_VERIFY_LEAF_SIGNATURE,SELF_SIGNED_CERT_IN_CHAIN,CERT_HAS_EXPIRED - The SSL configuration applies to all HTTPS communications between Infisical and your ADCS server
- Only HTTPS URLs are supported - HTTP connections are not allowed for security reasons

