- Set up and add secrets to Infisical Cloud
- Create an Azure Key Vault Connection
- Ensure your network security policies allow incoming requests from Infisical to this secret sync provider, if network restrictions apply.
The Azure Key Vault Secret Sync requires the following secrets permissions to be set on the user / service principal
for Infisical to sync secrets to Azure Key Vault:
secrets/list, secrets/get, secrets/set, secrets/recover.Any role with these permissions would work such as the Key Vault Secrets Officer role.Secrets in Infisical that contain an underscore (
_) will be converted to a hyphen (-) when synced to Azure Key Vault.- Infisical UI
- API
-
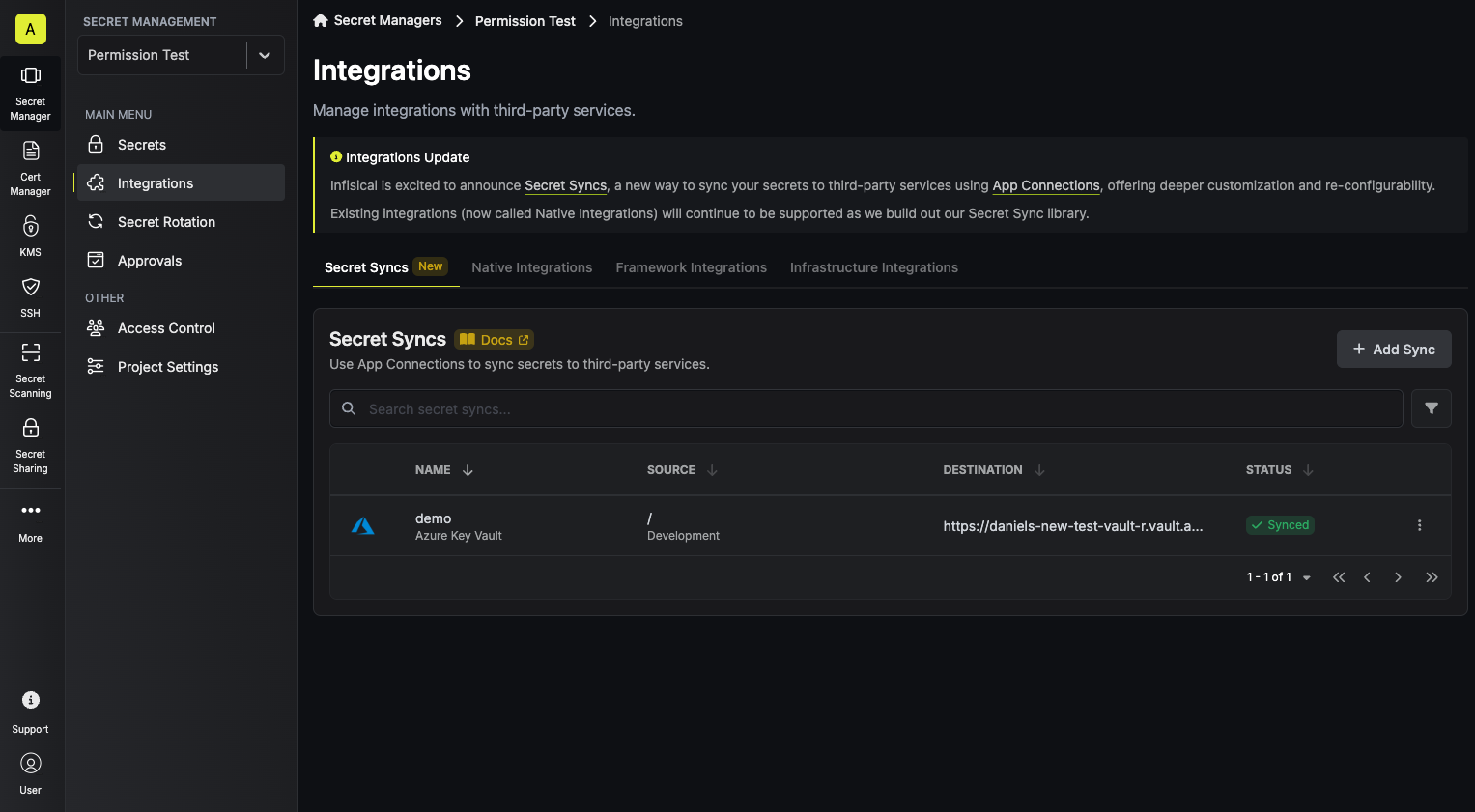
Navigate to Project > Integrations and select the Secret Syncs tab. Click on the Add Sync button.
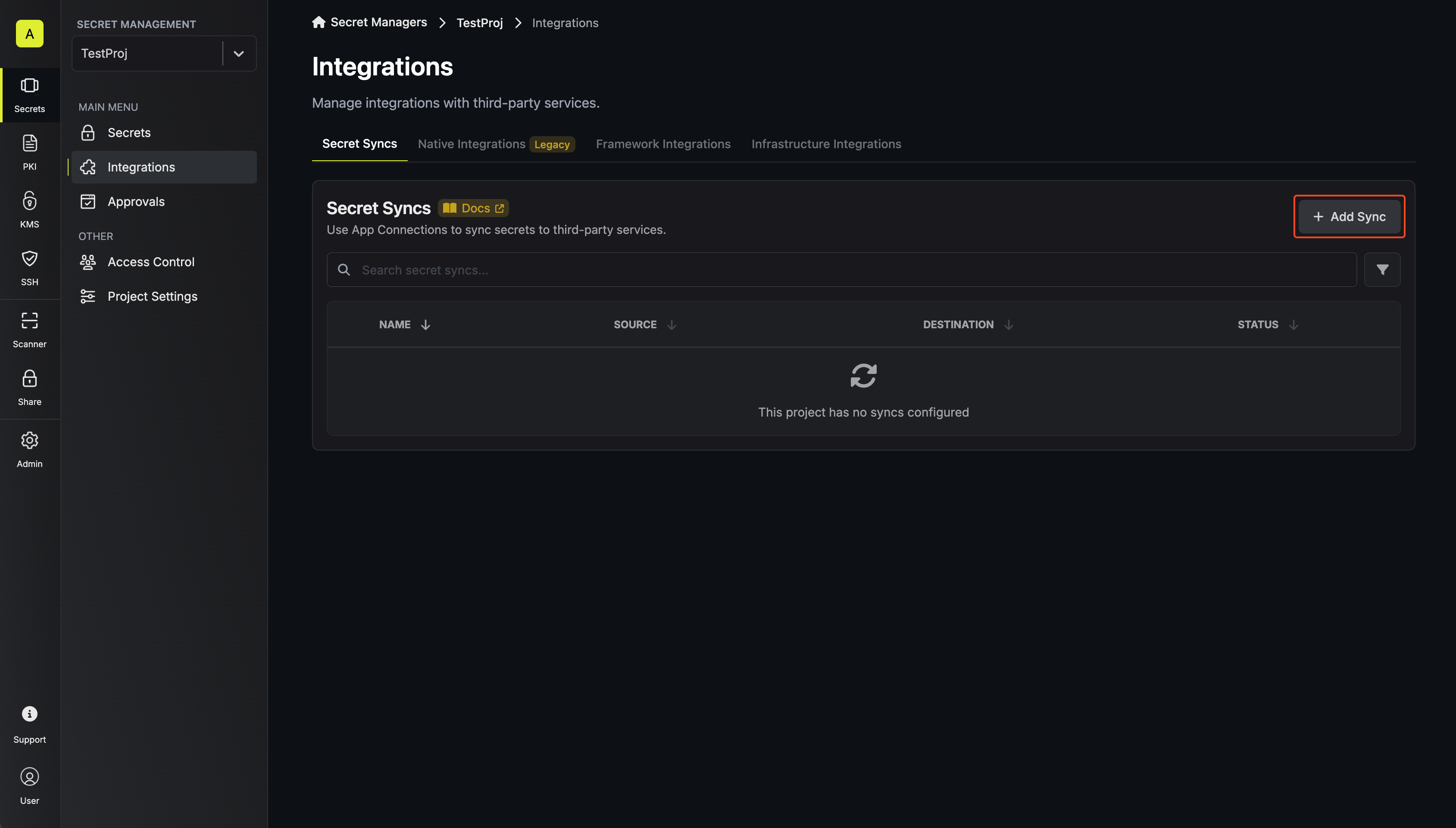
-
Select the Azure Key Vault option.
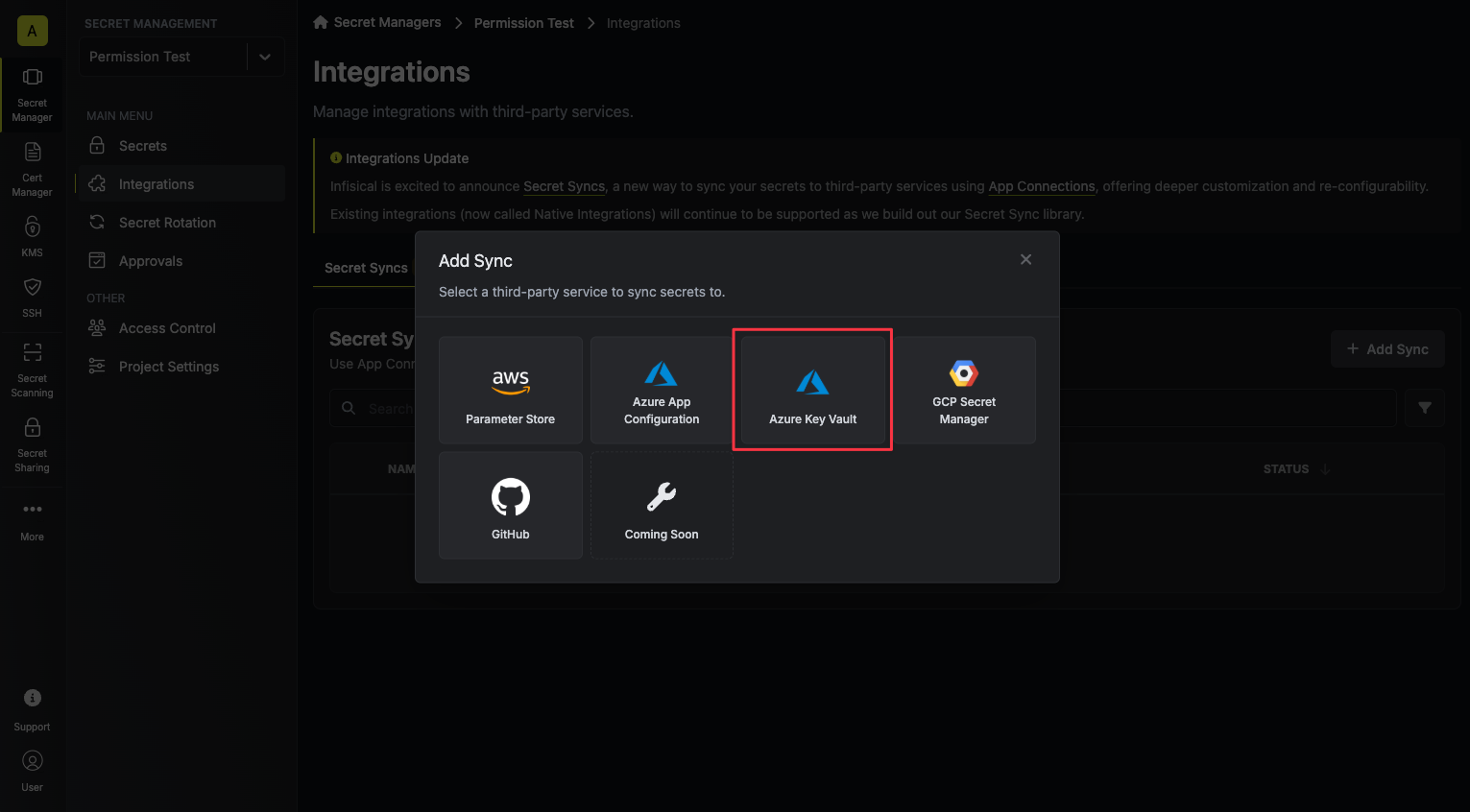
-
Configure the Source from where secrets should be retrieved, then click Next.
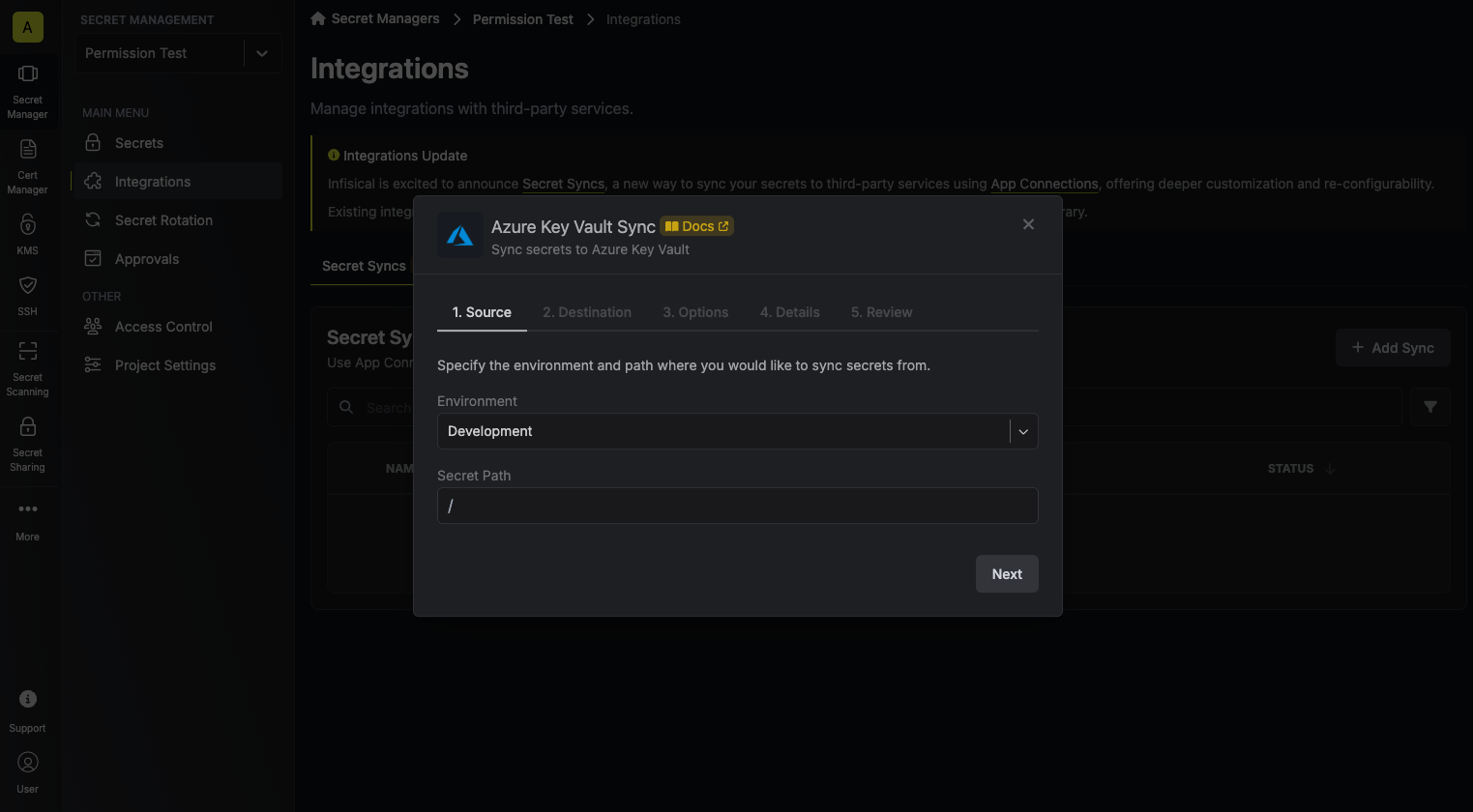
- Environment: The project environment to retrieve secrets from.
- Secret Path: The folder path to retrieve secrets from.
-
Configure the Destination to where secrets should be deployed, then click Next.
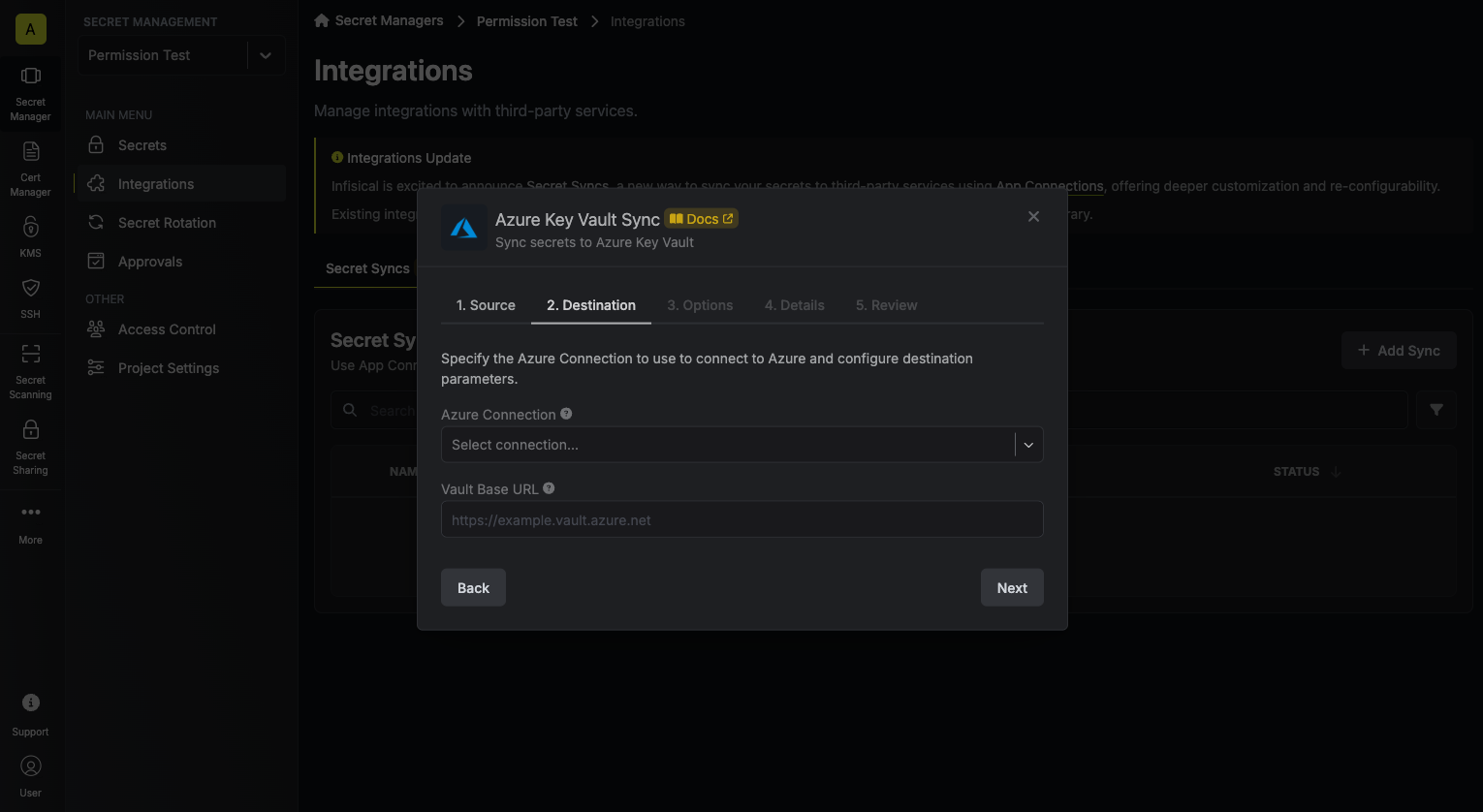
- Azure Connection: The Azure Connection to authenticate with.
- Vault Base URL: The URL of your Azure Key Vault.
-
Configure the Sync Options to specify how secrets should be synced, then click Next.
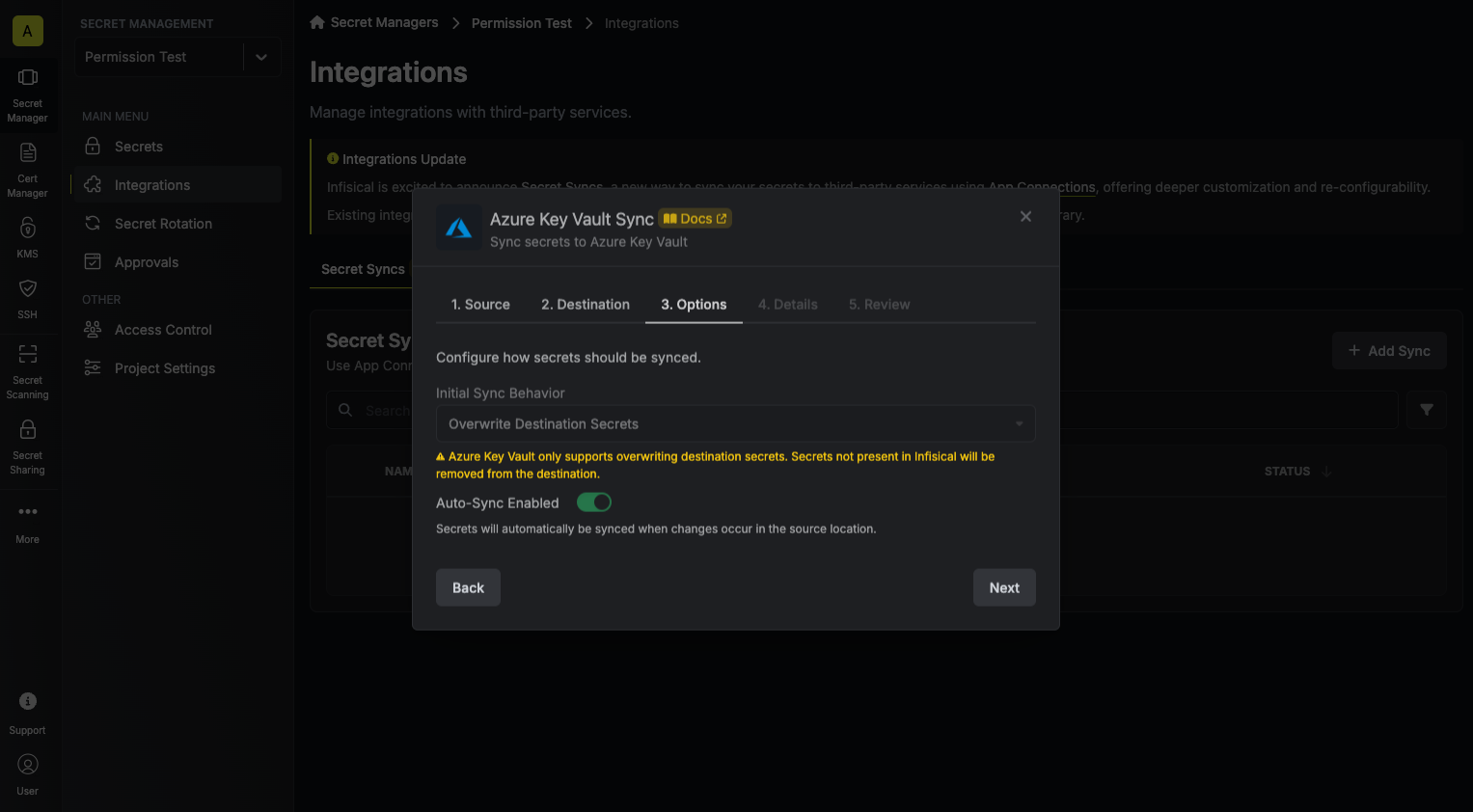
- Initial Sync Behavior: Determines how Infisical should resolve the initial sync.
- Overwrite Destination Secrets: Removes any secrets at the destination endpoint not present in Infisical.
- Import Secrets (Prioritize Infisical): Imports secrets from the destination endpoint before syncing, prioritizing values from Infisical over Secrets Manager when keys conflict.
- Import Secrets (Prioritize Azure Key Vault): Imports secrets from the destination endpoint before syncing, prioritizing values from Secrets Manager over Infisical when keys conflict.
- Key Schema: Template that determines how secret names are transformed when syncing, using
{{secretKey}}as a placeholder for the original secret name and{{environment}}for the environment.
We highly recommend using a Key Schema to ensure that Infisical only manages the specific keys you intend, keeping everything else untouched.- Auto-Sync Enabled: If enabled, secrets will automatically be synced from the source location when changes occur. Disable to enforce manual syncing only.
- Disable Secret Deletion: If enabled, Infisical will not remove secrets from the sync destination. Enable this option if you intend to manage some secrets manually outside of Infisical.
- Initial Sync Behavior: Determines how Infisical should resolve the initial sync.
-
Configure the Details of your Azure Key Vault Sync, then click Next.
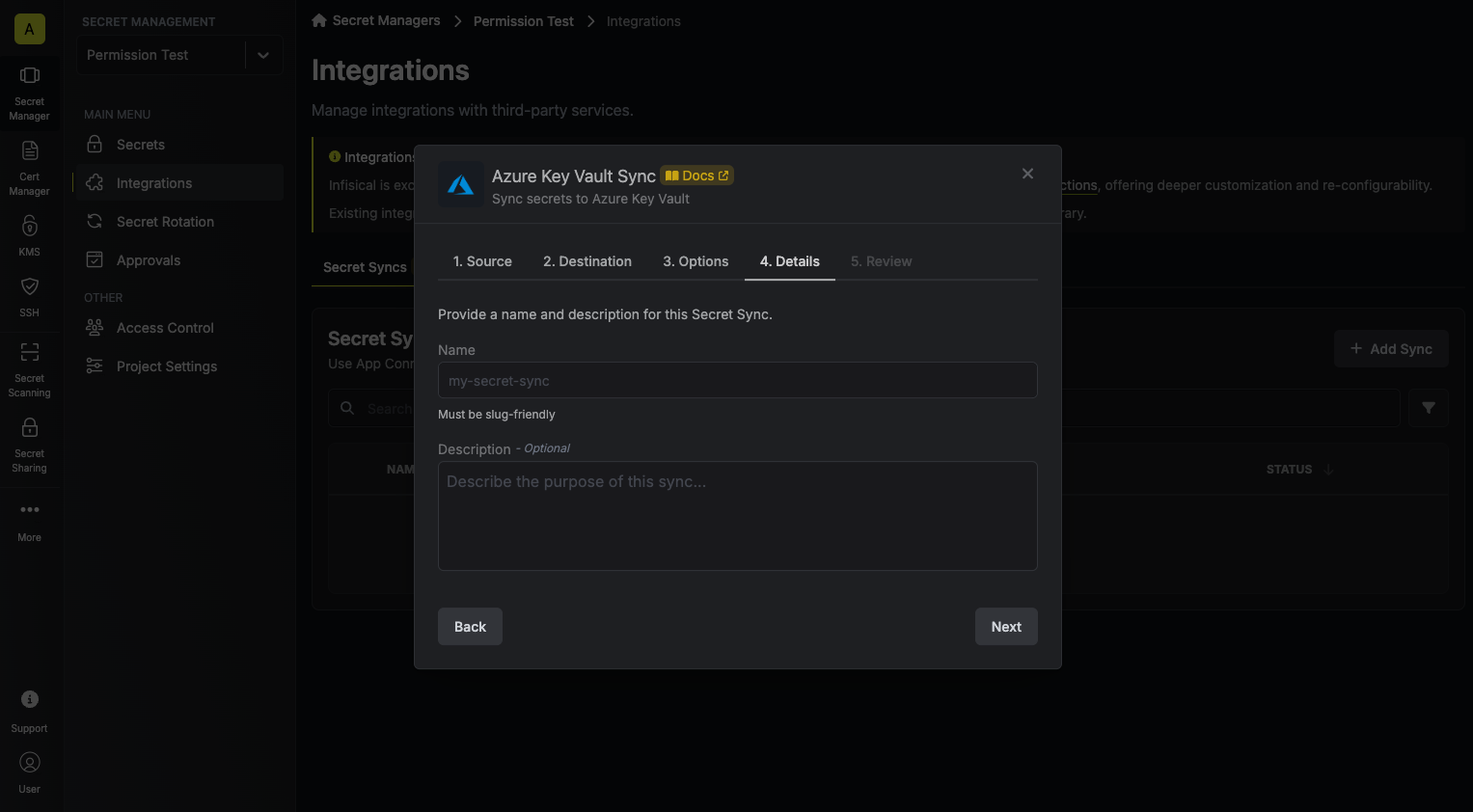
- Name: The name of your sync. Must be slug-friendly.
- Description: An optional description for your sync.
-
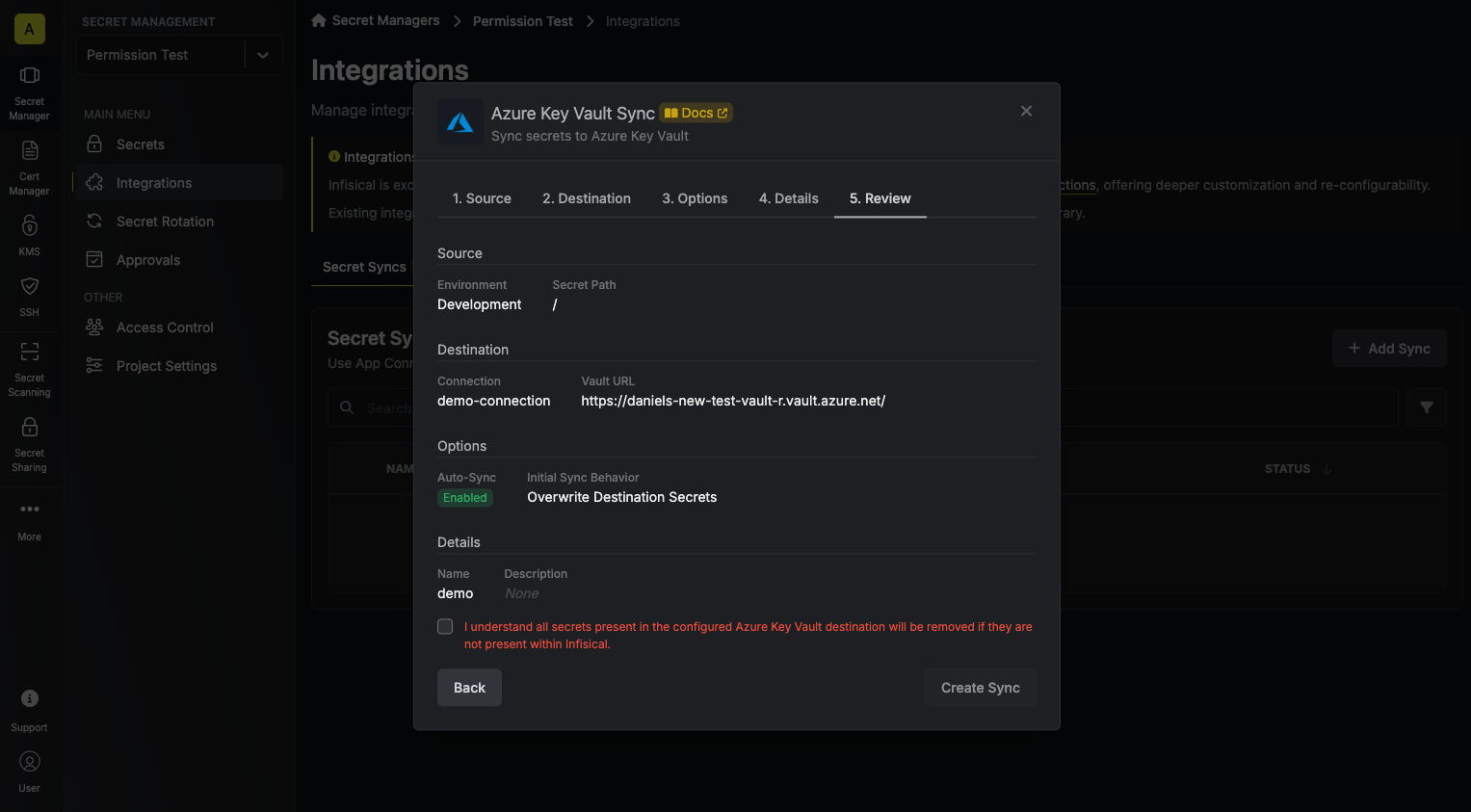
Review your Azure Key Vault Sync configuration, then click Create Sync.
-
If enabled, your Azure Key Vault Sync will begin syncing your secrets to the destination endpoint.